During the early days of the dot com boom, websites, server farms, and IT infrastructure were popping up in droves. Despite these great leaps forward a critical component was overlooked. This critical component is the security of these new devices and data being processed, something that is of utmost importance these days. Fortunately, we as a society came to our collective senses and decided that at least some sort of cybersecurity was necessary. Now our desktop PCs, laptops, and mobile phones benefit from basic virus scans and malware blockers, but with the rise of Internet of Things (IoT) devices, the game has changed and the floodgates have been opened to a new generation of digital threats.
The IoT is a network of devices that contain software and have the capability to connect to the internet, such as smart watches, security systems, and tracking devices. As technology evolves, more and more devices have become connected to the internet, with capabilities for remote access and control. Similarly, as artificial intelligence and voice search become more prevalent, virtual assistants like Amazon Alexa and other smart home devices will begin to play a larger role in people’s daily lives. Since these conveniences must be connected to the internet in order to function, they create a new vulnerability in cybersecurity that did not previously exist.
IoT Presents New Challenges for Security
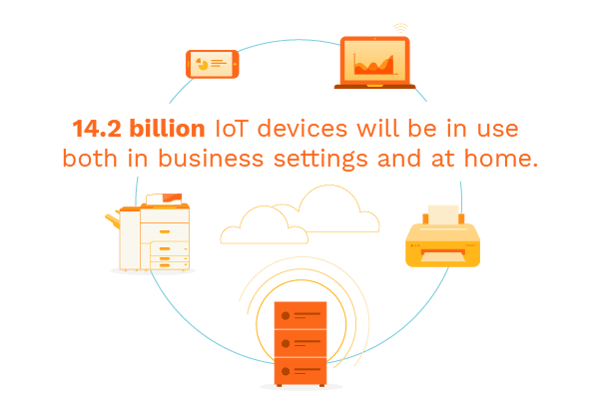
A Gartner study showed that in 2019, 14.2 billion IoT devices will be in use both in business settings and at home. While this is great news for users who love the convenience of smart technology, the trend presents significant risks: data loss, data theft, and privacy issues are definitely issues to be aware of when enjoying IoT technology. While the benefits of IoT can be immensely helpful in the office or home setting there are still the risks attached to using IoT technology.
Security Issues
IoT may be smart devices, but they certainly aren’t the most secure; many of them have shortcomings when it comes to protecting users. Lots of IoT technology still remain weak in terms of cybersecurity compared to the standard laptop computer. A recent OWASP study has shown that a lack of strong security is an issue that continues to plague IoT. A combination of weak passwords due to the assumption that IoT can’t be hacked, lack of strong network security, lack of physical hardening, and insecure data transfers are responsible for these lapses in protection. This lack of security allows hackers to crack passcodes and enter into these IoT devices, creating massive botnets that can comprise even the most secure system.
The first wave of IoT hacking occurred in 2016 during the Mirai Botnet attacks. In this case, the main targets were internet protocol (IP) cameras and routers, which were used to attack Dyn, a Domain Name Services (DNS) provider, which caused a bottleneck that blocked internet access for millions of users worldwide. Attacks on IoT devices are speculated to increase, as IoT devices become more commonplace and more varied; it’s projected that 25% of future hacks in enterprises will target IoT.
The Root of the Issue
The problem is that of basic security. While most internet-enabled IT devices (routers, security systems, etc.) come equipped with security features, few IoT devices enjoy this benefit. This inherent lack of security is the biggest driver of change in our cybersecurity landscape.
IoT devices produce new, and harder to detect, attack vectors for hackers and illicit users. It’s easy to tell when our laptops have malware, but what about our webcams? Or our copiers? These are typically devices we still associate as unconnected but now with connection comes these risks.
Furthermore, as more and more of our devices become connected to the internet, the risk of illicit surveillance increases greatly, whether at home or in a work environment. Devices such as televisions, kitchen appliances, thermostats, and cameras can all be hacked to spy on people in their own homes. Computer-controlled devices in vehicles, such as brakes, engine, hood and trunk releases can be vulnerable to infiltration as well, adding a physical threat to hacking.
The Changing Cybersecurity Landscape
Just as users realized they couldn’t use computers that weren’t equipped with antivirus protection, users of IoT devices are slowly realizing that internet connectivity can spell danger. In short, we’re getting smarter:
- Administrators of corporate IT networks are cracking down on which devices actually need internet connectivity and which don’t justify the increased cybersecurity risk.
- Businesses are gathering more information about each IoT device’s security lifecycle, from how firmware is upgraded to how bugs are patched.
- Network segmentation of IoT devices is becoming the norm to protect vulnerable endpoints. This involves partitioning each IoT device into secure segments that aren’t connected to traditional IT infrastructure, guaranteeing that should a breach occur, only the IoT device itself is affected.
Overall, the rise of IoT devices has made us warier and less willing to accept convenience for the sake of convenience, but the cybersecurity industry still has a long way to go. Security for IoT devices needs to become a priority and integrated into each system while the device is still in the design phase. Users need to be more vigilant about their internet-enabled toys and businesses need to implement good security practices across all employees, and the hardware itself to guarantee that they aren’t exposed to digital threats.
Categories: Security, Internet of Things