With the rapidly rising adoption of cloud technologies and the rise in cyber threats, it has become crucial for organizations to secure their cloud infrastructure and cloud-native applications. Cloud Security Information and Event Management (Cloud SIEM) is an emerging security solution that provides organizations with real-time security monitoring, threat intelligence, threat detection, and incident response capabilities for their cloud-based environments.
Sophos recently surveyed 4,984 IT professionals working for small-to-medium-sized businesses (SMBs) across 31 countries. The study focused on those who use Infrastructure as a Service (IaaS) to gain insights into the reality of cloud security operations for SMBs. The results revealed that SMBs using IaaS have faced significant changes in their cyberattack experiences.
Specifically, 56% of respondents reported increasing attacks on their organization, while 59% experienced an increase in the complexity of attacks. Furthermore, 53% reported an increase in the impact of attacks on their organization, highlighting the severity of the threat. Finally, 67% of respondents said their organization had been hit by ransomware, underscoring the urgent need for effective cloud security solutions.
This blog will explore Cloud SIEM and how it can help organizations secure their cloud environments.
What is Cloud SIEM?
Cloud SIEM, or Cloud Security Information and Event Management, is a security tool that enables real-time cloud infrastructure and application monitoring. By collecting and analyzing security-related security data from a variety of data sources, including network devices, servers, and endpoints, cloud SIEM systems can detect and respond to security incidents almost immediately.
Cloud SIEM platforms offered by Managed Security Services (MSS) providers follow a Software-as-a-Service (SaaS) model and leverage advanced analytics, Artificial Intelligence (AI), and Machine Learning (ML) technologies to identify and alert security teams about potential threats—for example, unauthorized access, data exfiltration, malware, and phishing attacks.
Cloud SIEM-as-a-Service providers empower IT teams with actionable insights, real-time alerts, and reports to quickly respond to security incidents and mitigate risks.
Cloud SIEM solutions seamlessly integrate with various cloud platforms and services, such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP). As such, they can quickly provide a centralized Security Operations Center (SOC) with dashboards concentrating on security monitoring and management across cloud environments.
Why is Cloud SIEM Important?
Cloud SIEM is essential because it's a proactive cybersecurity approach that helps fortify cloud infrastructure. Cloud infrastructure has significantly transformed threat detection and response protocols, particularly with the adoption of new cloud deployment models. The change in infrastructure and deployment models has resulted in new security models and attack surfaces that require new ways of performing threat detection and response.
One notable change is the responsibility model. With on-premises deployments, organizations were responsible for the entire security stack, from the physical Infrastructure to the data stored on it. However, with cloud infrastructures, the shared responsibility model stipulates that the cloud service provider is responsible for the security and maintenance of supporting hardware. At the same time, the organization is responsible for securing and maintaining data on those systems. This creates multiple opportunities for potential visibility gaps.
The dynamic nature of cloud workloads and workflows means systems can come and go rapidly. In this scenario, confidential information can be exposed to other users or the cloud service provider because there is no control over the existing hardware. Also, multiple access and management capabilities make managing, tracking, and auditing administrative actions challenging. As such, traditional monitoring approaches are no longer practical, and new controls must be applied.
From an attacker's perspective, cloud-based systems provide variability in administrative access models, allowing attackers to exploit two different angles of attack. They can access systems inside the enterprise network perimeter and escalate to an administrative account with cloud resources or compromise credentials from an administrator account with remote administrative capabilities or cloud administrative access.
Cloud-native SIEM offers a solution to these challenges by providing comprehensive visibility into the current state of security. It's designed to address organizations' specific challenges when transitioning to the cloud, making it an easy and effective solution.
What Are the Advantages of Leveraging Cloud SIEM?
Some of the key benefits of leveraging cloud-based SIEM solutions include the following:
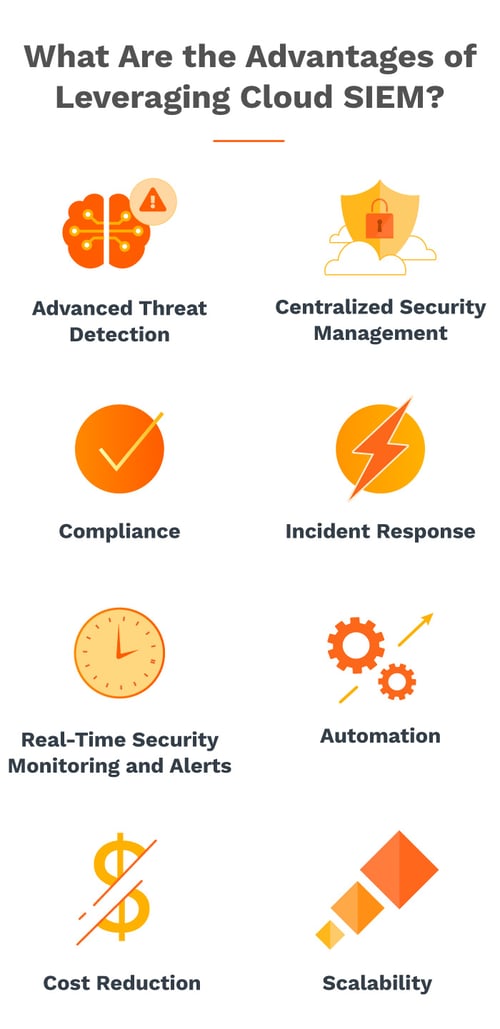
Advanced Threat Detection
Cloud-native SIEM uses advanced analytics, AI, and ML technologies to quickly identify and alert security teams about potential threats. This includes security events such as unauthorized access, data exfiltration, malware, and phishing attacks.
Centralized Security Management
Cloud SIEM helps enterprises monitor and manage security across multiple cloud platforms and services from a centralized location. This approach helps simplify security management and goes a long way to ensure robust security.
Compliance
Cloud SIEM helps organizations comply with regulatory requirements by providing centralized security monitoring and management and detailed audit security logs and reports. Comprehensive logging capabilities ensure compliance requirements of the likes of the California Consumer Privacy Act (CCPA), California Online Privacy Protection Act (CalOPPA), General Data Protection Regulation (GDPR), Health Insurance Portability and Accountability Act (HIPAA), Payment Card Industry Data Security Standard (PCI DSS), and Service Organization Control 2 (SOC 2) are met consistently.
Incident Response
Cloud SIEM provides IT teams with actionable insights, real-time alerts, and reports to respond quickly to security incidents and mitigate risks.
Real-Time Security Monitoring and Alerts
Cloud SIEM provides real-time monitoring of cloud environments, enabling organizations to detect security threats and respond to incidents quickly. On multiple levels, proactive threat detection (with advanced threat intelligence) allows IT administrators to stay ahead of malicious actors.
Cloud SIEM is important because it helps organizations secure their cloud infrastructure and cloud-native applications, detect and respond to security threats in near real-time, and comply with regulatory requirements. In the current threat landscape, where cyber threats are becoming increasingly sophisticated and frequent, Cloud SIEM is critical to an organization's overall security posture.
Automation
Automated tools manage the entire process of collecting security data. So, administrators don't have to spend valuable time doing manually intensive mundane activities such as searching through security logs or identifying potential threats.
Cost Reduction
Cloud-based solutions help reduce operational costs associated with physical storage systems compared with on-premise SIEM solutions.
Scalability
Scalable cloud architecture enables organizations to handle more data while providing robust security, easy access, and performance regardless of size.
What Are the Disadvantages of Leveraging Cloud SIEM?
Using cloud-based SIEM technology comes with certain drawbacks that organizations should consider. These include:
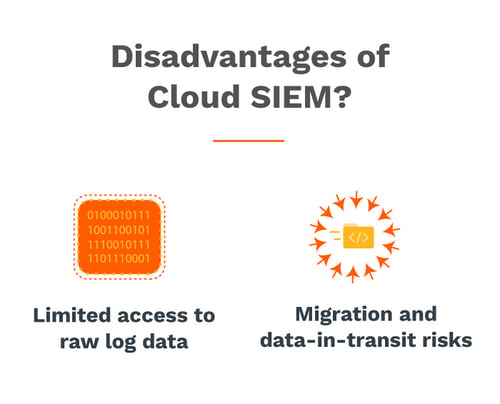
Limited Access to Raw Log Data
While the security data collected by cloud SIEM tools come from an organization's endpoints and systems, some vendors may limit access to this information. Instead, they may provide only aggregated reports based on the collected data.
As such, choosing a vendor that uses data lake architecture is important. This allows organizations to maintain their raw log data through their own log management protocols. This approach helps make data available for forensic analysis and audits. It also ensures the organization can access the information it needs for effective security monitoring and incident response.
Migration and Data-in-Transit Risks
When sensitive data is moved offsite, it's vulnerable to risks associated with data-in-transit, and organizations may also be exposed to compliance risks. However, many cloud SIEM vendors provide security measures, such as data encryption and strong authentication, to mitigate these risks.
Conclusion
In conclusion, cloud-based SIEM solutions are critical tools for businesses operating in the cloud. It enables organizations to meet the unique challenges of securing cloud-based systems, such as the shared responsibility model and the dynamic nature of cloud workloads.
By providing comprehensive visibility into the current risk exposure, cloud SIEM empowers businesses to detect and respond to potential threats quickly, ultimately improving their overall security posture.
As cloud adoption continues to increase, implementing cloud-based SIEM should be a top priority for any organization looking to secure its data and Infrastructure in the cloud.
Categories: Security, Cloud, Cyber Security, Cloud-based, Network Security, Proactive Network Security, Cloud Computing Security, Cloud Computing, Managed Security Services, IT Security, IT, Cybersecurity, SIEM, Cloud SIEM











