Data privacy and data protection might sound like the same thing, but they actually work in harmony to keep your business running smoothly.
These terms should not be used interchangeably. Data privacy refers to the rules and regulations regarding who has access to company data. Data protection is the process of securing data from unauthorized access. To put it simply, data privacy is the law and data protection is how that law is enforced.
The two facets are closely connected, and you need both in order to truly keep your data where it belongs — in your hands, not on the Dark Web or out in the open. The average cost of a data breach can be in the range of $3.86 million, showing how understanding the relationship between data privacy and data protection can be good for your bottom line.
While companies might focus on data protection, as data breaches and hacks get the scariest headlines, placing importance on data privacy can help stop issues before they become major problems.
But first, let’s outline what data privacy and data protection really are.
What is Data Privacy?
Privacy policies are more than just the blocks of text you scroll past in order to download an app or agree to an update. It might read like endless lines of legalese, but it is absolutely necessary for companies to outline.
Data, as online giants like Facebook and Google have shown, can be the most valuable asset a company has. Determining rules and outlining who has access to what are essential in today’s heavily digitized ecosystem.
Consumers are becoming far more savvy about data privacy. One survey of American consumers found that 73 percent of those polled said their concern about the privacy of their personal data has increased in the past few years. Social media was the least trusted industry with regard to data privacy, consumers said, with health care and banking among the most trusted.
As companies collect an increasing amount of personal, financial and other sensitive information, data privacy matters more than ever. Companies have to regularly reassess their data privacy policies to make sure they’re not lagging behind innovation.
In the medical world, data privacy rules are known as HIPAA, ensuring that patients’ data is safe. Not too long ago, companies that do business in the European Union had to update their regulations and policies to be GDPR compliant. These laws change from country to country, and even state to state, governing what info companies are legally able to glean from consumers.
These policies lay out how data is collected, who has access and how the company will use the data. All these laws and regulations relate to how information should be handled, based on their relative importance.
What is Data Protection?
If data privacy contains the laws, data protection is the law enforcement.
When data privacy becomes endangered, data protection is what stops it from becoming a costly breach. It’s more about the tools and technology in place to deter data thieves from gaining access to private information such as social security numbers, credit card numbers and more.
Data protection can often lag behind data privacy. That’s evident now, as companies are still trying to become GDPR compliant. In January (7 months after GDPR implementation started), ZDNet found that only 59 percent of companies believed they were fully compliant with the guidelines laid out by GDPR.
You’d be surprised how many companies lack quality data protection plans.
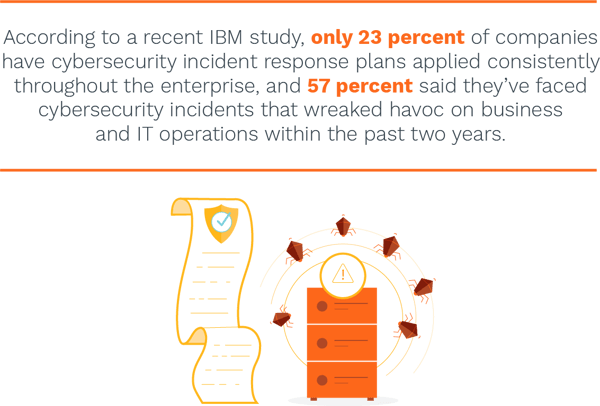
As hackers’ techniques grow more complex (and varied), all kinds of companies need to examine not only their own data privacy policies, but how they’re actively protecting consumers’ data. Especially in light of the upcoming holiday shopping season, when more transactions mean more chances for hackers to claim consumer data, protection has to be at the forefront.
With more employees in pretty much every vertical operating remotely (and on their own preferred devices), data protection has to be something beyond a task for IT to focus on. It should be a plan acknowledged by C-level executives, executed by office managers and known by employees.
Encryption is a major force for data protection. Encrypted data ensures a private connection between consumer and company, blocking data thieves out.
Hackers are just growing more aggressive, meaning companies have to take a proactive approach to data protection before it’s too late. Data protection has grown into something that should be a major focus across the board. This is a company security issue — not just an IT issue.
True data security combines an up-to-date data privacy plan that clearly outlines who has access to the data your company possesses, along with an aggressive data protection system in place.
Categories: Document Management, Data, File Storage











