The spread of the Coronavirus (COVID-19) has brought with it unprecedented changes in how businesses are run. As the government works on containing the virus, citizens are advised to stay at home as much as they can. In affected regions, employers have been advised to embrace work-from-home strategies to reduce the chances of infections in the workplace. If you are an IT expert, you could be interested in knowing how to manage network security with most employees working from home.
 Management of Network Security brings with it a big set of challenges when dealing with a remote workforce arrangement. With an understanding of the challenges unique to a remote workforce, it will be easier for the IT manager to put in place strategies than ensure network security for the employees and the office. If your company has fortified network security, your business can enjoy the benefits of communication and sharing of files. In this article, we share with you some valuable tips on how to manage network security with a new remote workforce.
Management of Network Security brings with it a big set of challenges when dealing with a remote workforce arrangement. With an understanding of the challenges unique to a remote workforce, it will be easier for the IT manager to put in place strategies than ensure network security for the employees and the office. If your company has fortified network security, your business can enjoy the benefits of communication and sharing of files. In this article, we share with you some valuable tips on how to manage network security with a new remote workforce.
How to Manage Network Security with a Remote Workforce
Equipped with the right information, IT management can ensure network security for the remote task force. Below are some measures you can take to manage network security with a new remote workforce.
1. Create and Document your Remote Access Policy
Adequate security for a business's information systems is a fundamental responsibility of the organizations' IT team. In the light of the COVID-19 pandemic, remote workforces dealing with sensitive information, safety, privacy, and defense need a clearly stipulated authorization control. The access control policy offers clear guidelines to all legitimate users of the network on a 'need-to-know' and 'need-to-use' basis. To get the access policy right the first time, you can reach out to a consultant or a freelancer who has helped other organizations with creating a viable network access policy to help you come up with the basic guidelines and requirements. Once the original policy document is in place, you can customize it to meet the unique needs of your organization then have the workforce agree to it before they are allowed to use the system. Always keep this policy document updated, taking note of changes in the workforce that may affect communication privileges.
A network policy is crucial because the organization’s employees present the greatest weakness in Network Security. To elaborate, the FBI estimates that between 2012 and 2018, Business Email Compromise alone accounted for the loss of over $12.5 Billion. Most of these network security breaches come in the form of emails targeted at employees with the attacker pretending to be a senior or a stakeholder, duping them into sharing sensitive information or money with the scammer. A network policy will help mitigate such breaches.

Once you come up with a clearly defined set of remote access rules, you should train the employees through emails and other media covers to make them appreciate their role in ensuring Network Security.
2. Secure Your Network Using VPNs
Virtual Private Networks are great for improving the security and privacy of network systems. VPNs provide secure information tunnels that give workers encrypted access to browse files stored on the organization's database securely. Which means anyone who intercepts traffic cannot read it. For VPNs to work, the IT team has to create and set them up. Companies with remote workforces have recorded an increase in the use of VPNs since the start of the COVID-19 outbreak.
If your business issues work computers to staff while working from home, you should consider using a VPN to secure communications between your office and employees. They securely tunnel internet traffic through selected servers, which is why most people use this technology to bypass restrictions on location-specific content. In cybersecurity, VPNs can be used to ensure online privacy.
However, if your company expects workers to use their personal home devices, a better solution would be to set up remote-controlled solutions between the employees' work computer and their personal computers. It only takes 15 minutes to set up, and the employee can remotely log in to their work computer from anywhere - and it's completely secure.
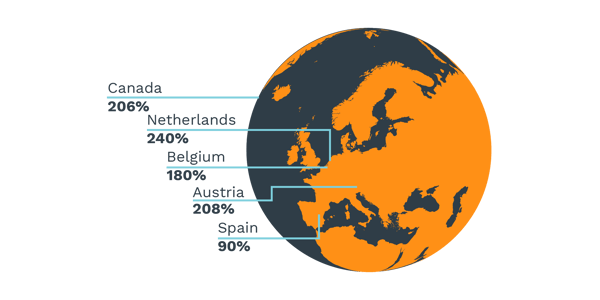
According to a recent revelation by NordVPN, following the pandemic, employee business VPN usage has increased by 240% in the Netherlands, 208% in Austria, 206% in Canada, 180% in Belgium, and 90% in Spain.
3. Make Use of Cloud Applications
Thankfully, most office applications have web-based equivalents. These are perfect for the remote workforce since they automatically update changes made to documents, offer improved security, and provide alternative backups. Cloud providers such as Google, Microsoft 365, and Amazon Web Services are more equipped to handle network and information security. That way, you transfer the burden of worrying about Network Security to your chosen provider. The IT team can focus on ensuring compliance by employees while the cloud provider ensures your network is secure from attacks targeting your employees.
4. Create a Strong Firewall
A significant solution to cybersecurity risks arising from remote connections is the setting up of a Firewall suitable for your organization's size and complexity. Firewalls will help the IT security team to monitor traffic, which enables you to catch any breach attempts as they happen. A good firewall should include features such as an impenetrable VPN, strong antiviruses, built-in-high-availability features, proxy servers, and packet filtering options. You should also set up employees with SOHO firewalls that run behind those provided by the ISP. This way, your employees' devices will always be isolated from others, even in the same networks.
5. Keep Your Devices and Software Updated
While updates can be annoying, they are important in maintaining data security. In 2017, a ransomware called WannaCry affected more than 200,000 Windows computers. The ransomware was created by the US National Security Agency (NSA), but hackers gained access to it and used system vulnerabilities to send malware to the affected computers. The attack was later fixed by installing security updates to the affected computers.

Software updates patch security flaws that hackers could use as points of vulnerability. They also add new and improved security features to ensure your systems and data are under the best protection. According to Norton, even the best anti-viruses are ineffective if their virus signature databases are outdated. Thus, keeping your devices up-to-date can help reduce the effects of an attack on your network.
6. Continuous Monitoring and Tracking of Office Assets
The level and quality of asset management will greatly influence the efficiency of your network security efforts. Asset management and employee monitoring become a challenge when dealing with a remote workforce. There are, however, various modern tools and techniques to keep company information and equipment under the radar at all times. These include geofencing, ticketing systems, and predictive asset monitoring. Cloud-Based IT management platforms enable office ICT managers to connect with company assets remotely so that they can be secured and monitored. With continuous monitoring and tracking, you are able to identify & respond to attacks on your network in real-time and observe compliance to remote access policies by your employees.
7. Enforce the Use of Strong Passwords
As an IT expert, you understand the importance of strong and unique passwords in protecting company data and networks. You should enact rules requiring colleagues to use passwords that are hard to guess and conform to your company's access policy. A strong password typically uses more than eight characters, combines numbers, letters & special characters. It is also crucial that employees change their passwords every few months to reduce the risk of having their credentials compromised.
Conclusion
We hope that this article provided adequate knowledge on how to effectively manage and safeguard network security with a new remote workforce. It’s essential to give your team the tools needed to succeed in network security and remain proactive to keep you worry-free as you embrace borderless business.
Categories: Security, Network Security, COVID-19











