Cyberattacks are now the norm. With data breaches and ransomware attacks hogging the headlines almost daily, robust cyber defense protocols are now more important than ever before.
According to a recent study by IBM and the Ponemon Institute, the average cost of a data breach was a whopping $4.24 million per incident this year. It's, in fact, the highest it has been in 17 years.
We can attribute the surge in security events to the following:
- Compromised credentials (which was the leading cause of data breaches in the study)
- The sudden rise in remote working
- Hackers now target all types of businesses, especially small and medium-sized businesses (SMBs)
A combination of the above can wreak havoc on any business. But when it comes to SMBs, a cyberattack could cripple operations and disrupt business continuity or even lead to bankruptcy.
As legacy antivirus (or AV) solutions and firewalls simply don't secure your environment (anymore), organizations need a different approach to defend against potential attacks.
What Is a Next-Generation Antivirus (NGAV) Solution?
NGAV or next-generation antivirus software leverages a combination of cutting-edge technologies like artificial intelligence and machine learning algorithms to detect and eliminate potential threats more efficiently.
This approach is more effective because NGAV protocols concentrate on detecting malicious behavior. In this scenario, the machine learning algorithms examine the apps, data, end-user behavior, processes, and network activity to identify suspicious behavior.
The key difference between NGAV and traditional AV solutions is that the former is proactive, while the latter is reactive.
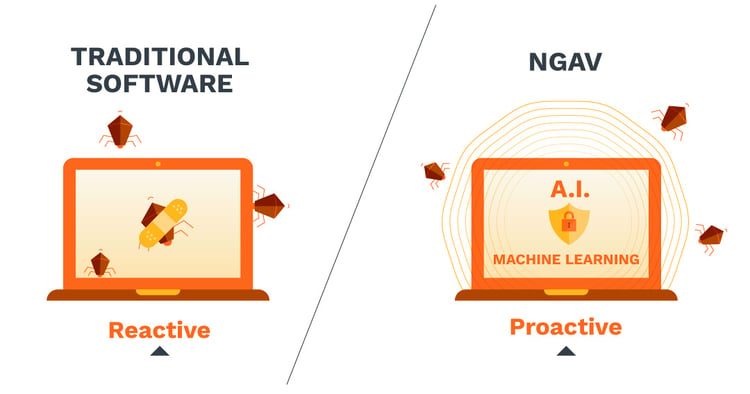
For example, traditional antivirus solutions are signature-based and can only detect attacks that have occurred before. The security product vendor then rolls out a patch to update the system and protect users from further attacks.
This means that traditional antivirus software only protects you from known malware and other threats. Your infrastructure is essentially wide open to a breach for any new technique used by threat actors.
What Is Traditional Antivirus Software?
Most people are familiar with traditional AV software because they often come installed on personal and enterprise devices. As traditional antivirus demands user direction to initiate actions, it's safe to say that most have some experience with it.
However, this legacy approach to cybersecurity is ineffective against rapidly evolving advanced threats that are common today.
Traditional AV solutions are simply no match against the following threats:
- Advanced ransomware attacks
- Macro-based attacks
- Memory-based attacks
- Multi-vector and fileless malware attacks
- PowerShell scripting language
- Remote logins
Traditional antivirus doesn't protect businesses from these types of unknown threats as they don't introduce new files into the system. As a result, malicious files and code can go undetected by legacy software that searches for known file signatures.
In a modern enterprise IT environment, traditional antivirus solutions lead to significant gaps in your corporate security posture. Virtual endpoints lack broader contextual intelligence, so they can't adequately protect your enterprise security architecture.
To fortify your IT infrastructure, you must complement your security protocols with comprehensive, consistent, and coordinated security tools that successfully mitigate risk. In other words, that traditional antivirus software you depended on for decades probably won't cut it anymore.
Do You Need Next-Generation Antivirus Protection?
NGAV effectively overcomes the limitations of legacy antivirus solutions. It's an excellent way to proactively mitigate risk in the current threat landscape. This next-gen protection protocol also comes with its own library of known threats, but unlike traditional antivirus software, it can think on its own and doesn't require human intervention.

However, do you need a next-gen antivirus solution? The answer is almost always a resounding "yes!" But it really depends on the organization's use case and current antivirus solution.
You might not even have to replace your traditional antivirus solution because you can add NGAV to complement it. After all, enterprises still need protection from known threats or signature-based threat detection.
The type of NGAV you go with will also depend on your industry-specific regulations (for example, HIPAA and PII). When assessing a potential NGAV solution, you should look for the following:
- Levels of false positives
- Robust malware protection
- Cutting-edge ransomware detection and protection
False Positives
Next-gen antivirus software strives to detect unknown malware and defend your infrastructure; this is much harder than working with a set of known threats. As a result, you will have some false positives to manage, and that's not always a good thing.
Whenever you implement an NGAV solution, look beyond the vendor's list of malware and check the configuration. Security products come with varying abilities, and this approach will help you better understand the software's actual false positive rate.
Malware Protection
Leading next-gen protection leverages advanced machine learning algorithms and predictive analytics to identify new attack methodologies. So, you won't have to wait around for a patch to protect your infrastructure.
However, it's important to test the abilities of your NGAV software regularly against a set of advanced persistent threats. As almost half of the attacks use fileless malware leverage scripting languages like Microsoft's PowerShell, you should take a deny-listing and safe-listing approach. This is because your IT administrators will use these scripting languages both heavily and daily.
Ransomware Protection
If your NGAV software doesn't boast an effective mechanism to defend against brand new ransomware strains, it's effectively rendered useless. It's important for your next-generation antivirus software to autonomously detect them, initiate remediation, and manage new threats still unknown to the greater cybersecurity community.
In this case, you need an endpoint security solution to make this process easier. Endpoint detection and response (EDR) tools monitor your infrastructure in real-time. They are also intelligent enough to identify malicious activities and respond to them effectively.
It’s always better to combine different security products to take advantage of each tool’s key functions and related benefits. For example, a threat intelligence solution like EDR or endpoint detection and response tools are essential because they help identify potential threats in your networking environment and respond to them effectively.
EDR protocols can analyze the threat and provide detailed information about how it was initiated and which parts of the network were affected by it. It will also inform your IT security team what it's currently doing and how you can stop the attack altogether.
As EDR contains the threat as soon as it's detected, it will stop it from spreading across the entire enterprise network or the cloud. This approach helps secure all the devices connected to the network, even during zero-day attacks.
Upon completing a thorough investigation, your EDR solutions will eliminate the threat. As such, this next-gen tool does a whole lot more than your old-school antivirus software. Furthermore, EDR is also a great way to reduce the number of false positives generated by your NGAV tool.
Next-gen antivirus tools like endpoint protection platforms (EPPs) also target potential threats as they try to enter the perimeter of your network. Although it's almost impossible for EPP to detect all the potential threats coming through various network connections, it still helps. EPP still adds another layer of security to fortify your security posture.
So, it's always a good idea to combine both EDR and EPP with your NGAV software to improve your cybersecurity posture. This approach will help you secure all potential entry points and make it much harder for threat actors to breach your network.
Categories: Security, Artificial Intelligence, IT Management, Network Security











