How often should you change your passwords? Every week? Every month? Every year? If you're still using a password like "password123," the answer is immediately!
If you're like most people, you're probably using the same or a similar password for a long time now. Despite the real threat of recycling passwords, you might be even using the same password for years.
With the number of apps and platforms we use in our daily life, updating passwords can be an exhausting undertaking. But updating your passwords might be the only defense between you and a hacker who wants to steal your data.

Why Should I Change My Password?
The answer to the question depends on your current password. If you're already using a unique, complex, and strong password, there should be no reason to change it right? Well, again, it depends.
If you have used the same password on more than one platform, then you should change it right away. If you're still using that (weak) password you came up with in high school, you should update it with a new password that meets the following criteria:
- A unique combination of numbers, special characters or symbols, upper and lowercase letters
- Password length matters, so always choose a password with more than 11 characters
- No common words or phrases
- No company-specific or self-identifying information like birthdays or addresses
- Not a duplicate password used in another account
If your current password meets the criteria above, do you still need to change it? Well, you guessed it, it depends.
When Should I Change My Password?
For more than a decade, security professionals established a password policy that demanded us to change passwords routinely. They used to enforce this through IT policies that demanded that we change passwords every 30, 60, or 90 days.
However, this didn't go to plan. Instead of helping to ensure password security, it left the whole exercise in a terrible state. This is because employees already had too many passwords to remember.
Whenever corporate policies were too strict, employees ended up writing down the passwords. We should have expected this as people often skirt the rules to keep doing their jobs with minimal disruption. This means that they continued their same bad password practices at home and at work.
The good news is that the National Institute of Standards and Technology (NIST) no longer recommends numerous password changes. In their Digital Identity Guidelines, the NIST recommends decreasing both password complexity and the volume of forced password changes.
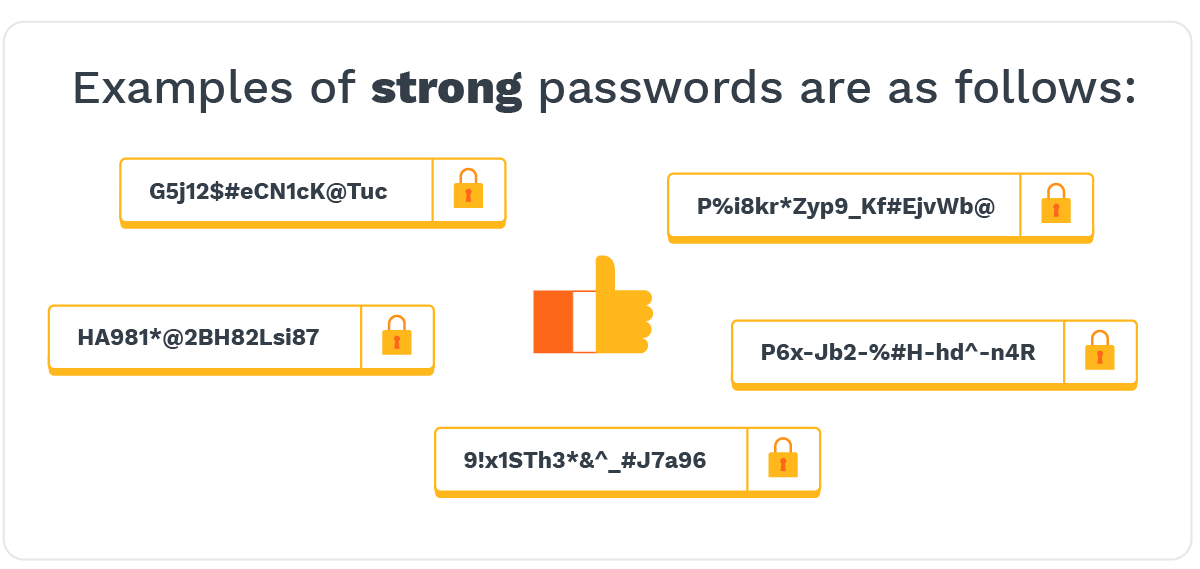
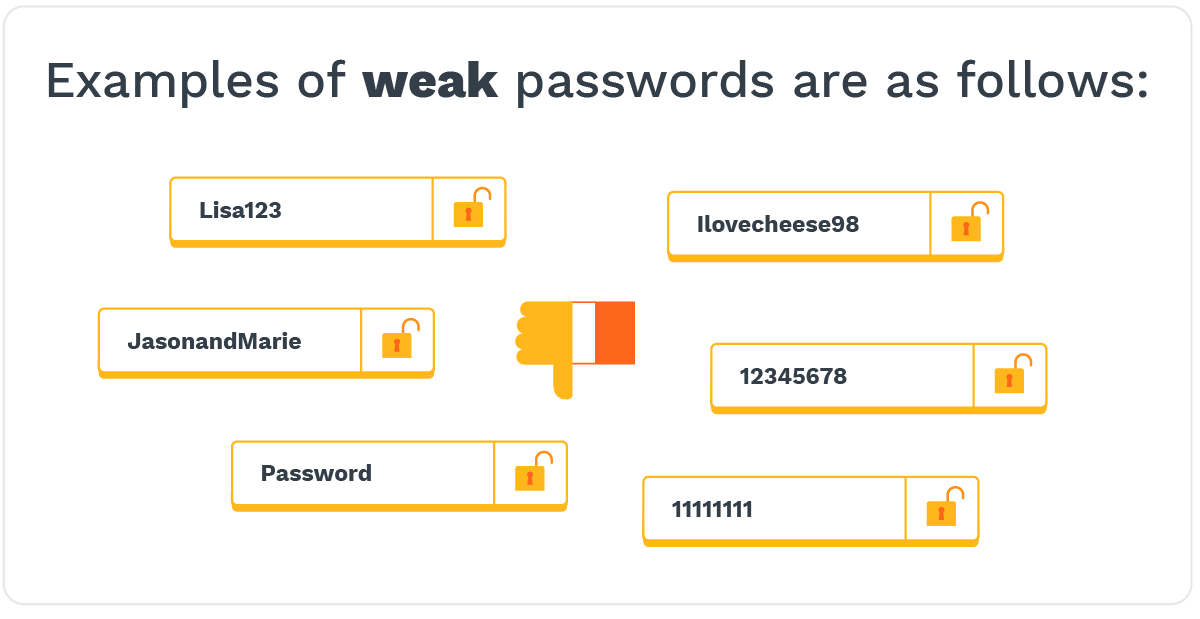
If you have a weak password with common words, names, addresses, birthdates, and phrases, please make sure to change it. It's also important to never reuse the same strong password on another platform.
It's also better to use passphrases than passwords, as the former is longer and harder to crack. Passphrases are also easier to remember. However, you must make your passphrase stronger by using both lower and uppercase letters, numbers, and symbols. For example, you can turn "Ilovecheese98" to "iL0v3CheE5eE98."
But if you already have a strong and secure password, when should you change it?
You should change your password if the service you're using disclosed a data breach. In this scenario, you should change your password as soon as you receive a data breach notification. At the same time, if you receive an email notifying you that someone accessed your account and it wasn't you, again, change your password right away.
You should also change your password if you found malware running rampant on your system. Often, the passwords used on that system will be compromised. But if you have a robust security solution that catches the malware before it takes effect, you should be safe.
Other reasons to change your password:
- You used your password on a public or shared computer (and you don't know if it was running a keylogger)
- You shared a password with someone else
- You haven't used an account in more than a year
- It's been more than a year since you updated your password
Choosing a strong password helps better secure your accounts, but it's not enough. It'll also help to leverage two-factor authentication (2FA) or multi-factor authentication (MFA) to fortify your security posture.
What Is the Ideal Password Policy?
The NIST's latest password policy guidelines state the following:
- The minimum password character limit is eight, and the upper limit is 64
- Your password shouldn't have any common words found in a dictionary
- Establish a sensible limit of online passwords
- Always check your password against lists of breached or pwned passwords
- Password complexity should be allowed but not enforced
- Don't enforce password rotation
- Users should change passwords whenever they're compromised or when they suspect that it's compromised
How Do Passwords Get Hacked?
Cybercriminals have several ways of hacking passwords. They are also continuously trying new ways to breach enterprise systems.
The easiest way to get a password is to buy compromised user information on the dark web. There's big money involved in this type of crime, driving criminals to compromise more accounts. So, if you're still using the same password after several years, there's a high probability that it's compromised.
However, if they haven't managed to hack into your email account or couldn't find it on an aggregated black-market list, bad actors will try to use one of the following methods to hack your password:
- Brute force attack
- Dictionary attack
- Guesswork
- Malware
- Ransomware
- Mask attack
- Offline cracking
- Phishing
- Rainbow table attack
- Shoulder surfing
- Social engineering
- Social media attacks (by impersonating platforms)
- Spidering
As hackers are always trying to compromise systems, it's vital not to store any of your password details in plain text on your device or in the cloud.
How Do I Know If My Password Was Compromised?
If you're not sure if your account details were compromised, there's a quick solution. You can check if your email or phone data was involved in a data breach by going to Troy Hunt's Have I Been Pwned website. You can also find out by using the Google Chrome web browser.
 Password Security Best Practices and Tips
Password Security Best Practices and Tips
Just like anything in cybersecurity, password security also demands that you follow best practices. These include the following:
Always Audit Your Passwords
Sometimes we may have used the same password on more than one account without realizing it. As such, it's best to audit your passwords to make sure that it's always a random combination of numbers, letters, and symbols. This could be part of your overall cybersecurity risk assessment.
Always Use Strong Complex Passwords
The weakest link is always people. As a result, it's crucial to emphasize the importance of password security and the need for strong, complex passwords.
Engage in Employee Training
As humans are the weakest link, you should always engage in regular cybersecurity training. By conducting regular security training, your staff has a better chance of staying alert to social engineering attacks like phishing campaigns.
Always Use Multi-Factor Authentication
Always use some form of multi-factor authentication like SMS (for 2FA) or Google Authenticator. This approach helps secure your account if your password is compromised.
Use A Password Manager
Let's face it, none of us will remember every strong password we come up with. Writing it down would require you to store it in a secure location, and this can get complicated when you need immediate access to your accounts.
The good news is that a password manager can act as a password vault that securely holds your login credentials. A good password manager will not only store and manage all your passwords, but it can also generate new ones. You can use tons of strong and unique passwords and not worry about memorizing even one of them.
All you have to do is save every password you have on the password manager and then secure all of them with one master password. So, instead of remembering all the passwords, you just have to remember one. Or you can even use biometric data to access your password manager.
Once set up, all you have to do to login into an online account is to simply type the master password into the password manager, and it'll auto-fill in the rest.
What Is A Password Manager?
A password manager is an encrypted digital vault that stores all your secure password login information. Whether it's apps, accounts, websites, or other services, you can access all your login details with one master password. Sometimes, you can also use your fingerprint or PIN to autofill this information in a form or password field.
There are three leading types of password managers:
- Stateless
- Token-Based
- Locally installed or offline password managers
Stateless Password Manager
Stateless password managers generate random passwords using a master passphrase and a tag leveraging a key derivation function. Whenever you use a stateless password manager, you won't be storing passwords in a database (which equals improved security). However, there's no sync option, and it's also more vulnerable (than other passwords managers) to brute force attacks.
Pros:
- It doesn’t store passwords in a database
- Often generates strong passwords
- User-friendly and affordable
Cons:
- No sync options
- More vulnerable to brute force attacks
- Single point of failure
Token-Based Password Manager
Token-based password managers require users to provide both their login credentials and the security token for that device. It's a local piece of hardware that works like a key to unlock your account. Using a master password with a token is an excellent idea as it also adds two-factor authentication.
Token-based password managers provide a higher level of security with multiple levels of authentication. However, they are also more expensive than other types of password managers. They can also be highly complex for non-techy users.
Pros:
- Hardware-based and more secure
- Fine-grained access management and control
- Tokens are stateless
- Two-factor authentication adds an extra layer of security
- Works across devices
Cons:
- More complex and best suited for tech-savvy users
- More expensive
Locally Installed or Offline Password Managers
Storing login credentials locally on your computer or mobile device works if you encrypt the data. However, you can only access those accounts from a single device. This approach provides the user with complete control of their password data.
If you have to save the same information on multiple devices, you increase your risk exposure. If a hacker specifically targeted you with malware (to log keystrokes), they can breach your device (and accounts).
You can also choose to write down your account and password details the old school way in a notebook. However, this approach comes with the risk of losing this information, and so on.
It can also quickly become frustrating if you manage multiple accounts because you have to key in your password manually.
Pros:
- Cost-effective/free
- It can be more secure than storing passwords in the cloud
- Provides users with complete control of access data
Cons:
- At risk of physical damage or theft
- It can be a challenge to manage multiple accounts
- No way to sync across multiple devices
- Single point of failure
Adopt Password and Cybersecurity Best Practices
As cyberattacks are relentless and targeting everyone on the planet, targeting everyone on the planet, businesses need to do whatever it takes to stay a step ahead. As such, it's crucial to adopt not only good password habits but also cybersecurity best practices.
So, if you're reading this and wondering about password security, change your password if it has been more than a year. Although everyone may not be happy about this approach, it's necessary to secure your sensitive data. While you're at it, it's also a good idea to schedule a password security training session to get everyone in the company on the same page.
As threat actors keep relentlessly targeting everyone on the planet, businesses need to do whatever it takes to stay a step ahead. As such, it's crucial to adopt not only good password habits but also cybersecurity best practices.
Categories: Security, Office Hacks, Cyber Security, Network Security, Proactive Network Security, IT Security











