When we think of hacking, we can sometimes think of cyber geniuses who managed to break into untouchable systems. But the majority of successful hacks are pulled off by people who know as much about computers as their victims.
Social engineering leans on human experiences and emotions to coax people into doing something they shouldn’t. As the name implies, the approach taps into how people relate to one another to manipulate a user into a certain response. We’ll look at how this scam works and how you can prevent attacks.
What Is Social Engineering?
Social engineering is a somewhat broad definition, but the idea is to exploit how people think. The scammer is essentially manipulating a person into doing something specific, typically for one of two things:
- Disruption: The criminal will want to corrupt data to hurt the company (and likely ask for a ransom in return).
- Steal: The criminal will directly steal money, information, or exclusive access.
With social engineering, the bad actor is hiding both their identity and motive in an attempt to exploit another person for their own gain. They rely on human emotions to motivate people to do what they want. In other words, these criminals use subtle maneuvers to gain a person's trust somehow and then exploit it.
How Does the Cycle Work?
There are a few key steps that we see again and again with social engineering:
- Information is gathered about the individual or company being targeted.
- Infiltration occurs with the goal of establishing a relationship or sense of trust.
- The attack is advanced by exploiting the victim's weaknesses.
- The criminal disengages after the victim takes the desired action.
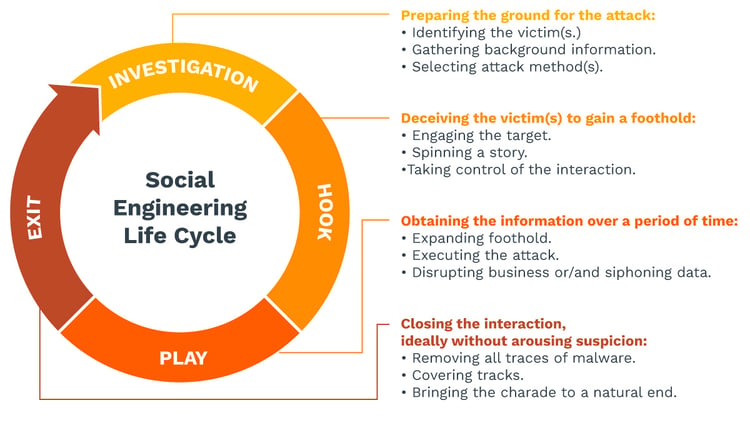
It might be a single fake phone call or email, but sometimes it's social media conversations that take place over the course of months. Once in a while, it's an in-person affair (though this is much rarer). In some cases, there's no interaction at all. For instance, a criminal might look over an employee's shoulder when they're in a hotel room or coffee shop and watch their keystrokes.
Once the hacker has achieved what they were looking for, they cut off communication. This 'achievement' might mean downloading malware that instantly announces itself to the victim, so the employee knows instantly that they made a mistake.
More often, though, the infiltration or error isn't immediately detected. Maybe the hacker simply verified a key detail (e.g., the employee's date of birth, etc.) and plans to use it next month. Maybe the hacker installed scareware that lies in wait until the system is the most vulnerable.
Traits of Social Engineering
There are a few important traits of social engineering that can be used to spot an attack:
- A play on emotions: Social engineers are likely to appeal to a person's sense of fear, excitement, anger, sadness, or guilt.
- Act now: Any time-sensitive demand, whether it's a prize that needs to be claimed or a problem that requires immediate attention, should be verified before anyone takes action.
- Believability: Criminals are confident when they ask for information. If they're not believable, they won't be able to get very far.
While some social engineering campaigns are perpetrated against thousands of people in hopes that one or two will stick, others are incredibly complex. It might mean months of research about a single employee: where they live, who their boss is, what time they show up for work, what coworkers they interact with regularly. That kind of information is exceptionally helpful to a person who wants to establish credibility and can really improve a criminal's odds of success.
Hackers don't need to know very much about computers with social engineering — they only need to know how people use computers. This form of criminality is often used as part of larger criminal campaigns to infiltrate bigger systems.
Social Engineering Techniques, Tactics and Examples
We'll start with definitions and then flesh them out so you can see how it works in the real world. Common types of social engineering include:

- Email spamming: Most people know that they should avoid spam, but some messages will still slip through.
- Phishing: A phishing scam relies on sending legitimate emails to people and requesting their personal data.
- Baiting: Baiting can rely on external devices as a means to install malware. However, this verb can also refer to anyone who is trying to coax another person into believing a certain scenario (e.g., a fake seller on eBay with a great rating).
- Vishing: Sometimes called voice phishing, this scam will impersonate a legitimate phone number. The scammer on the other end will pretend to be anyone from a friend to a coworker.
- Smishing: A smishing attack will be sent via text messages or SMS. Because people generally trust their smartphones, this technique can be very effective at getting victims to reveal their sensitive data or account information.
- Pretexting: Pretextending is a general term that refers to anyone pretending to be someone else to gain anything from financial information to a Social Security Number. This form of social engineering is one of the most popular — and one of the most effective.
- Quid pro quo: A quid pro quo type of social engineering attack will ask someone to trade information for a specific purpose.
The most important part of social engineering is that whatever the scam happens to be, it somehow appears credible. The cybercriminal is trying to bypass anything from advanced antivirus software to just people's general sense of suspicion. To do this, they typically rely on either personal data or plain old human nature.
For instance, if you see a USB device on the ground, your first thought might be to wonder if someone lost it. You might think that by plugging it in, you could find who it belongs to. The cybercriminal who planted that USB knows that people will want to solve the mystery, which is why they left it there in the first place.
Or they might tell a person that they won a free cruise or a new iPhone. They might reach out to a person on social media and tell them that they've been chosen to get a new product from one of their favorite companies.
Another common tactic is sending emails from a fake email address disguised as someone a person knows. So a hacker might look up different names on a company website and then send ransomware to employees under a VP’s moniker. Or they might pose as a friend and ask the recipient to donate to a charity they're passionate about.
A cybercriminal might also pretend to be a tech support employee and request a person's login credentials to solve a problem. This quid pro quo tactic creates a sense of urgency in an employee and makes them that much more likely to hand over the information without even thinking of the ramifications.
Once people catch on to any given trick, the criminal will simply move on to a new social engineering technique.
How to Prevent a Social Engineering Attack
For small business owners, it’s impossible to fully prevent all attacks on your computer systems. No matter how much security awareness training you give to employees, there’s always a chance that a criminal out there will come up with a brilliant scheme that no one could have predicted.
That being said, there are ways to drastically reduce your odds of a social networking faux pas. In this list, we look at not only how to help employees become more aware of the risks of social engineering, but we also examine how to prevent social engineering from happening in the first place.
Don’t Click
Links in an email or text message are undoubtedly tempting, but employees must learn how to resist the urge to click on everything. Double-checking the source of the link or typing it in instead of clicking on it can go a long way to help employees avoid malicious websites or scareware.
Implement MFA
Multi-factor authentication (MFA) is a great way to reduce the odds of a hacked email account or bank account. Because so many people use the same passwords again and again, this technique uses more than one way to verify a person’s identity. MFA can be anything from biometric identification to standard security questions.
Monitor Employees
Employees are paid to do their jobs — not to learn the latest trends of hackers or the many (many!) types of malicious software available. Still, regular training can help employees be aware of what to look for in the event of social engineering. Ideally, the immediate response to anything that asks for personal data should be either to deny or delete.
Identify and Protect Your Key Assets
Hackers are going to go after the most prized information in a phishing email or vishing phone call, which could be anything from credit card numbers to tax documents. Having additional layers of protection for the most important information can go a long way to keeping that data safe. When you’re prioritizing security based on your critical assets, it’s a lot easier to protect your livelihood. We also recommend constantly monitoring your computer systems as well, ensuring that emerging vulnerabilities can be identified day or night.
Block Attacks with a Firewall
The best kinds of attacks are the ones that disappear before they reach anyone’s attention. A cloud-based firewall can be used to both prevent attacks and alert you to potential threats. These powerful programs can drastically slash your odds of a successful spoof.
Insist on a VPN
With so many employees working remotely, a Virtual Private Network (VPN) can secure your communications and encrypt sensitive information. Allowing people to use their own wi-fi, particularly when they’re out and about, is a recipe for trouble.
Try Penetration Testing
A penetration tester will identify the gaps in a system before a malicious party can. If the tester can access the critical systems, it’s a clear sign that other people will be able to as well. Along with updating your software and having all your SSL certificates in place, testing can play an important role in preventing malicious code from breaking in.
Turn on Spam Filters
Spam filters can’t catch every malicious link or email, but they can flag certain messages as suspicious. It makes it easier to cut down on inbox clogs, so you can focus on the information (and people) who really matter. Plus, it can free up employees’ time if they don’t have to carefully comb through it all.
Verify Phone Calls
It's difficult to know exactly who's on the other line, but there are clues about whether you're talking to a trusted source. If anything about the person seems fishy, particularly if they're making a request they've never made before, it could be a sign you're speaking to someone who has no intention of helping.
Key Takeaways
The real crux of preventing these attacks can be boiled down to vigilance. The more aware you are of social engineering, the less likely it is to happen to you or your employees. This includes giving employees the tools they need to make smarter decisions, of course, but it also comes down to how well you're preventing these attacks in the first place. The fewer criminals break through your network barriers, the better.
Categories: Security, Cyber Crime, Online Scams, Network Security, Proactive Network Security, IT Security, Email Security











