In an increasingly digitized world, companies operate online more than they ever have before. However, as our IT environment grows more and more complex, it becomes evident that the traditional methods of protecting corporate networks no longer provide the level of security needed.
The internet is a dangerous place with cybercriminals lurking around looking for the slightest opportunity to blast through weak spots in your IT security systems. Once a vulnerability is found, your system is open to harmful viruses, data breaches and cyber-attacks that put both your operations and your reputation at risk. But with the support of a more advanced security system, such as a Unified Threat Management (UTM) firewall, not only is the likelihood of your systems being attacked greatly reduced, but your company’s security operations as a whole become much more streamlined and efficient.
What is Unified Threat Management?
Unified threat management (UTM) is an all-in-one approach to information security. Instead of using separate point solutions for each security function, UTM uses a single piece of hardware or a cloud-based software to provide multiple security functions. This simplifies managing your information security by giving you a single management and reporting point instead of managing multiple security products from various vendors. UTM appliances have gained popularity because they simplify installation, configuration and maintenance of IT security systems.
With UTM, time and money are saved as the need for multiple appliances, each devoted to a separate security function are eliminated. Additionally, it eliminates the need for personnel to know how to monitor and operate each separate device. Because of UTM, your network administrators can now run and monitor all your security defenses from one computer.
Horror Stories
There are many situations where security breaches could have been detected earlier, with the support of an advanced security system such as UTM.

Most notably, one of the largest data breaches in history occurred just last year, in May 2019. The incident happened at First American, the largest real estate title insurance company in the US.
Almost 900 million records were leaked, including mortgage documents and personal identifying information. What made the incident more shocking was that a real estate developer attempted to warn the company of the security breach, but was dismissed. This highlights the importance of an advanced and consistently updated security system, as well as an awareness of the importance of taking such precautions.
More recently, since the outbreak of the Coronavirus, the World Health Organization (WHO) has suffered a drastic increase in cyber attacks. Almost 500 active credentials were leaked online. Additionally, hackers impersonated the WHO in fraudulent emails sent to the public seeking donations. The WHO has since been working towards strengthening internal systems and establishing more robust security measures.
Why UTM is Needed Now More Than Ever
The COVID-19 pandemic has caused a massive shift towards working from home. As the alternative workplace with a mix of in-office & remote employees quickly becomes the norm, the cybersecurity risks involved grow more serious, including phishing scams, data lass, and corporate espionage. Online threats have greatly increased, as much as six times the regular levels in the first few weeks of the outbreak. In March 2020 alone, phishing attempts increased by over 600%.

This increase can be attributed to an increase in the number of endpoints (devices such as laptops, mobile phones, desktops), which are potential points of entry to a corporate network. Thus, the shift to remote work enables cybercriminals to exploit endpoint vulnerabilities and access a company’s network with more ease.
Cybersecurity has become a priority, and worldwide IT spending on security has increased drastically. Moreover, as the IT environment grows more complex, more advanced security systems are needed to provide efficient protection. To maintain security in this time, there are numerous tasks that a security system must complete: inspect and manage traffic, block viruses and malware, detect and prevent potential attacks, prevent unauthorized access… the list goes on and on. Evidently, the traditional approaches taken in securing corporate networks are no longer sufficient.
In the past, companies would implement standalone security devices, each of which would address a different threat. Not only is it difficult to manage a patchwork of independent devices, but this setup can actually create the opposite of the desired effect, and reduce network visibility and performance. Because the different technologies lack central management, they cannot communicate well with one another. Additionally, data from the different devices are not compiled to allow for a holistic view of the network.
Therefore, the need for a service such as UTM, one that helps companies navigate the changing online environment, becomes more apparent. A UTM firewall system abolishes the need for onsite network security, and efficiently secures all endpoints with a remote workforce. It provides centralized control, a holistic view of network security, and simplifies the management of the security system.

Why is a UTM Better Than a NGFW?
UTM systems and next-generation firewalls (NGFWs) are often considered to be comparable. But in reality, they aren’t. NGFWs were developed to close the network security gaps that were left open by traditional firewalls. A NGFW will usually provide protection against DoS attacks, intrusion prevention systems and application intelligence. However, when alone, NGFWs cannot provide you with the multiple layers of network security that a UTM firewall system can give you in one place by including:
- NGFWs
- Anti-virus protection
- Spam filtering
- Deep packet inspection
- Data loss prevention
- Application layer firewall and control
- Web proxy and content filtering
- Security information and event management
- Intrusion detection and prevention systems
- Virtual private network
A UTM firewall system simultaneously fulfills the following outcomes:
- Priority processing: critically analyzing threats and determining which problems should be tackled first.
- Proactive potential: not only detecting and reacting to existing threats, but also hypothesizing about future issues and obstacles.
- Programmatic protection: using AI and automation to efficiently address cyber threats, and also to handle repetitive tasks that are typically done manually, such as data entry.
UTM is applicable universally, with all sectors and enterprises, whether small or large. It is much more efficient to stop cyberattacks at the entry point, before they have infiltrated the network; a UTM firewall system functions as a checkpoint, managing all entries, amongst its other numerous functions.

How Does UTM Do it All?
So, how can a single UTM firewall system replace multiple devices and do everything you need to protect your information systems and keep it easy to use and monitor? It’s simple, by using inspection methods that are used on all different types of security threats:
- Flow-Based Inspection
Flow-based inspection is used to sample data as it enters the UTM device. Using pattern matching, the device determines if the data flow contains malicious content. This inspection method does not fully reconstruct all elements, but rather analyzes the data in chunks, thus reducing the quantity of data that the UTM must inspect. As there is less data processing involved, the primary advantage of flow-based inspection is speed. However, it is less thorough when compared to proxy-based inspection.
- Proxy-Based Inspection
Proxy-based inspection functions by reconstructing the content as it enters the UTM device, conducting a complete inspection to identify any potential security threats. Rather than selecting samples of the data, as with flow-based inspection, it analyzes the full contents of the data. If the content is clean, the device sends it to the user. But if a security threat or virus is found, the suspect content is removed before the URL or file is sent to the user. The main benefit of proxy-based inspection is that it provides a higher level of security and analyzes the content in more detail, resulting in a higher likelihood of catching malicious content. However, this approach takes more time and can decrease network throughput, as it demands more processing power.
The Future of UTM
The global UTM market has experienced significant growth, and will continue to grow exponentially. From 2019 to 2025, the market has a predicted compound annual growth rate of 14.5%.
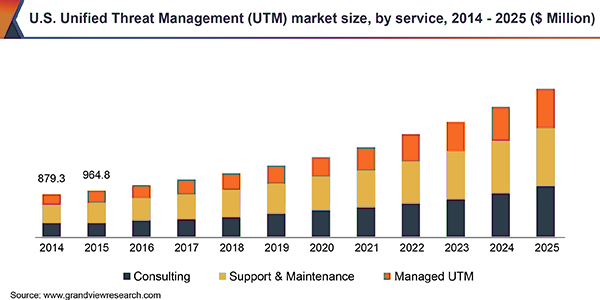
In an increasingly connected world, there are many opportunities for cybercriminals to make their move. The threats facing businesses in an online environment grow more sophisticated, as do the technologies developed to combat these threats. Particularly in light of the shift towards remote work, it is vital to establish strong, robust security measures that protect companies from informational, financial and reputation damage.
Categories: Security, Unified Threat Management











