Even when companies invest in securing their data and networks, they often make one mistake.
They forget to train their users.

Sure, everyone in a company receives instructions to create a strong password, not to log-in to public WiFi while accessing confidential information, and not to click on anything suspicious in email.
Then they're turned loose to work.
That's not really training.
- When's the last time you changed your password – and do you even know what a strong password is?
- Do you know why accessing public WiFi can endanger your network?
- Have you ever had a training session about how to identify “anything suspicious” in an email?
If you answered “no” to those questions, you're making the same mistake. Here's how you can do better.
Why Is User Training for Security Important?
How's this for an answer?
Research from IBM shows that roughly half of data breaches are caused by employees. A small portion of these are malicious – deliberate theft or a disgruntled employee sticking it to their boss. Mostly it's because people are clueless about information security. Forrester research shows a similar story, with 46% of data breaches from internal issues – malicious intent at 46% and accident at 42%.
We'll focus on how you can avoid those accidents from happening.
It doesn't matter how good your security plan and infrastructure is when all it takes is for one employee to click on a malware link in a phishing email and – BAM! – ransomware just got into your network (though you have a solid data backup plan, so that's not a major problem for you – read more).
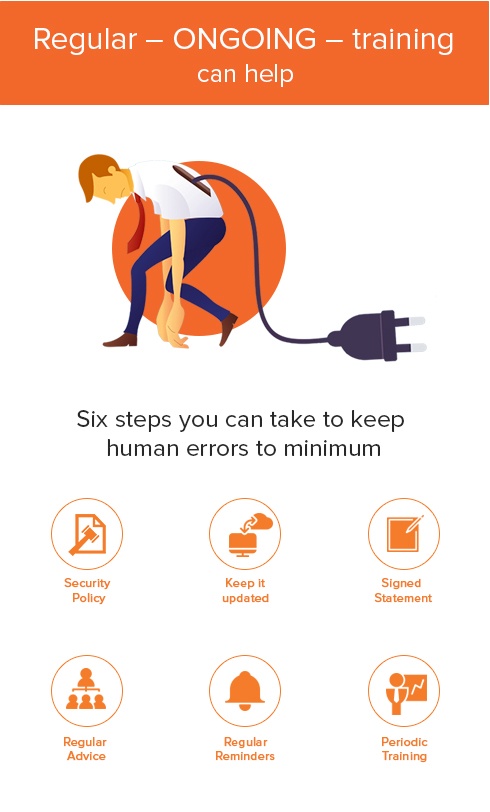
Regular – ONGOING – training can help alleviate this problem. Notice I said “alleviate” as human error is something we can't do away with! Here are six steps you can take to keep those human errors to a minimum:
- Create a security policy
- Keep it updated as new technology and apps come into use
- Ensure everyone in the office acknowledges that they understand the security policy by having them sign a statement
- Provide tips and advice on a regular basis
- Remind everyone throughout the year that cyber security is important
- Provide periodic training on key topics throughout the year – passwords, how to spot a phishing email, how to secure your mobile device, etc.
Training is effective. Research from Wombat Security and Aberdeen Research found that “an investment in user awareness and training effectively changes behavior and quantifiably reduces security-related risks by 45% to 70%.”
Remember that awareness isn't training – there's a gap between telling someone security is important and showing them how to, for example, spot a phishing email. So while it's important to tell everyone that you want to have a security culture, you also need to devote time to training so that everyone has the skills and knowledge to create that culture of security.
Don't Forget Physical Security
While you focus on cybersecurity, don't forget to physically secure your information. A few quick tips to keep in mind:
- Restrict access to your server room
- Don't let deliverymen wander your office unaccompanied
- Have employees keep keys or passes secure
- Lock drawers, file cabinets, and rooms where you keep sensitive information.
- Don't write passwords on a Post-it note and put them on your monitor or a bulletin/whiteboard (especially if you video conference regularly with that bulletin board or whiteboard in the background).
- Secure your laptop, phone, and other devices in public by keeping them near year and don't leave them in a locked car if you can help it.
Explain “Why”
One last note on security, training that explains the reasons for the security steps that need to be taken is more effective than a “just do it or else” approach.
A research paper, Technology Use: Conception and Operational Definitions, showed that “mindful” teaching worked better than “directive” training. Everyone is familiar with directive training, you sit in a room and someone explains what you should and shouldn't do. In this case, how to spot phishing emails using some key characteristics of those emails.
The “mindful” teaching shared how to spot a phishing email, but also why it was important not to click on them (harmful viruses, ransomware, etc.). The people in this group didn't recognize 100% of phishing emails, but were less likely to fall victim to an email scam.
For your office, this means sharing the dangers and risks with employees of the negative effects of a security breach on the business (and, in the worst case scenario, on their jobs).
Security is a strategy supported by information technology. It also should be part of your business culture.
Train regularly and stay safe.
Categories: Security, Office Hacks, Managed Services