Phishing attempts, bogus attachments, compliance violations: there’s a lot to think about when it comes to your emails. Whether you’re the CEO of a conglomerate or an individual trying to avoid hackers, we’re here to recommend practices that will keep trouble at bay. So without further ado, let’s jump right in.
What exactly is email security?
Email security is a broad term that describes the many procedures and tactics for protecting both the email account and the content of each email.
Why are your email security best practices so important?
Email security is a critical part of your overall cybersecurity. It’s not just the content of the email that’s important. You might think that since you’re not emailing state secrets, there’s no need to be vigilant about who has access to the information.
Yet hackers don’t just use your email for the content — they can use your account as a gateway to breach the larger network. From there, it’s a hop, skip, and jump to anything from confidential medical records to bank routing numbers to proprietary information.
What Are the Most Common Threats?
Before delving into this, you should know that cyberattacks are always evolving, depending on everything from network bugs to social engineering tactics. In other words, hackers can be both very smart and very creative, which can make it difficult to keep up with them.
That being said, there are ways to arm yourself with the right information before you click on something you shouldn’t.
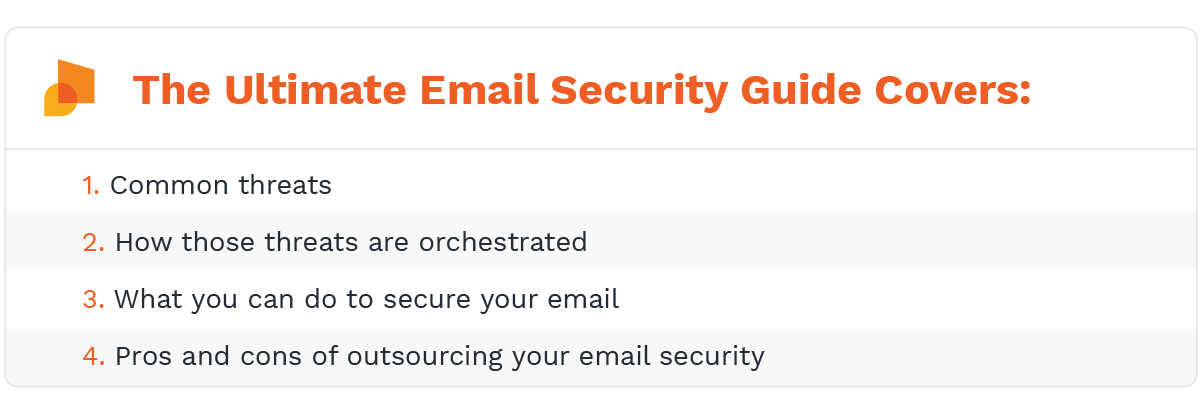
Phishing & Spear Phishing
Phishing refers to any attack that asks for money or otherwise valuable information (account numbers, passwords, etc.). A spear phishing attack is one that uses your information to get it (e.g., an impersonation of your friend or spouse).
Social engineering
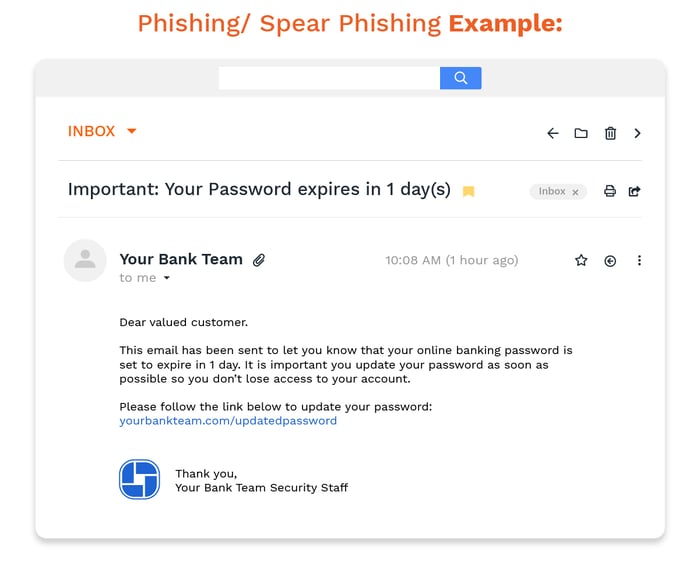
Hackers and phishing emails count on people idly surfing around when they’re tired or stressed. And it works. Social engineering is defined as any kind of persuasion that could cause people to click on a malicious email, attachment, or link.
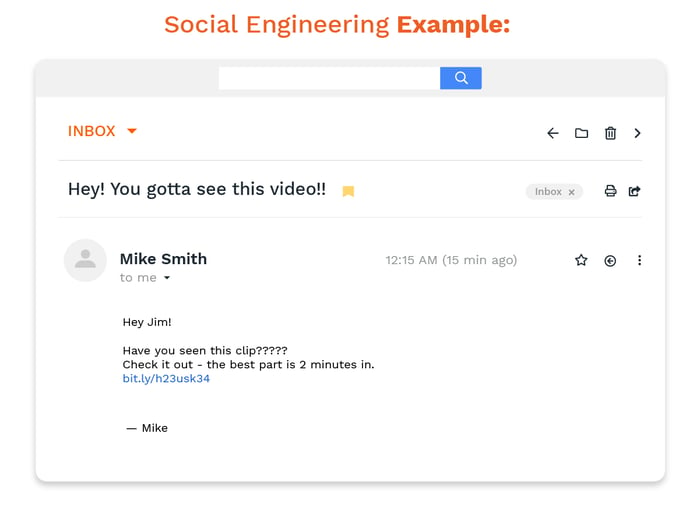
Social engineering is related to spoofing, where a person will provide false data to appear legitimate (e.g., sending an email from apple.com, etc.) While statistics vary, there are some reports that claim nearly a quarter of all successful attacks come from this threat.
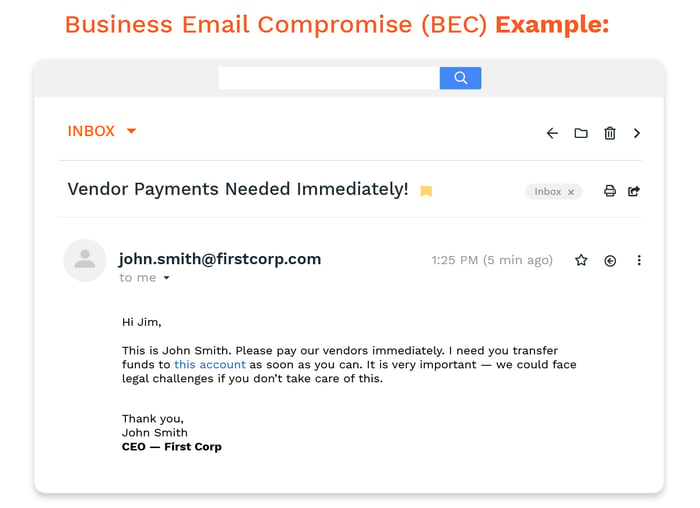
Business Email Compromise (BEC)
A BEC is a more specific type of spear phishing, one where the hacker pretends to be the boss of a company or another high-level executive. In this case, the scammer is studying the habits of employees to make the email appear that much more legitimate. The result is a fairly effective scam to steal anything from money to proprietary information.
Spam
We tend to think of spam email as annoying rather than dangerous, but there are ways to include malicious links, malware, trojans or other security threats in an otherwise innocent-looking advertisement. Spam may be sent by a bot controlled by a hacker or directly from an individual.
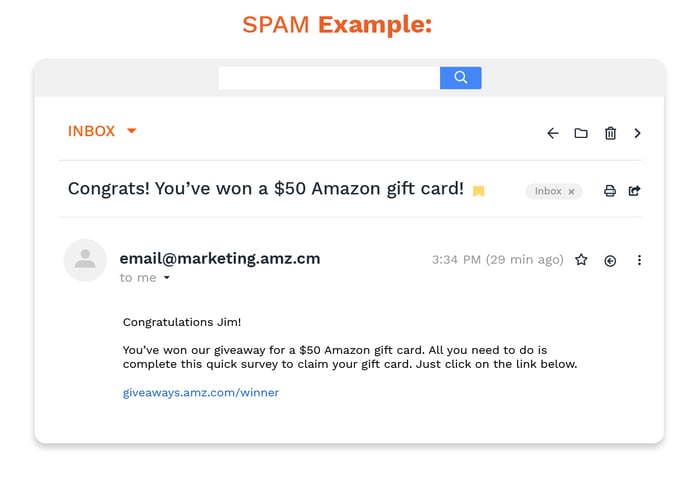
Malware
Malicious software (shortened to malware) can refer to ransomware, trojans, or any program designed to attack your systems. Ransomware is designed to encrypt your files or your entire operating system. To get them back, you’re asked to pay in a cryptocurrency (though there’s no guarantee that anything will be restored). Trojans are a specific type of malware that will give a hacker full access to your machine — including your webcam.
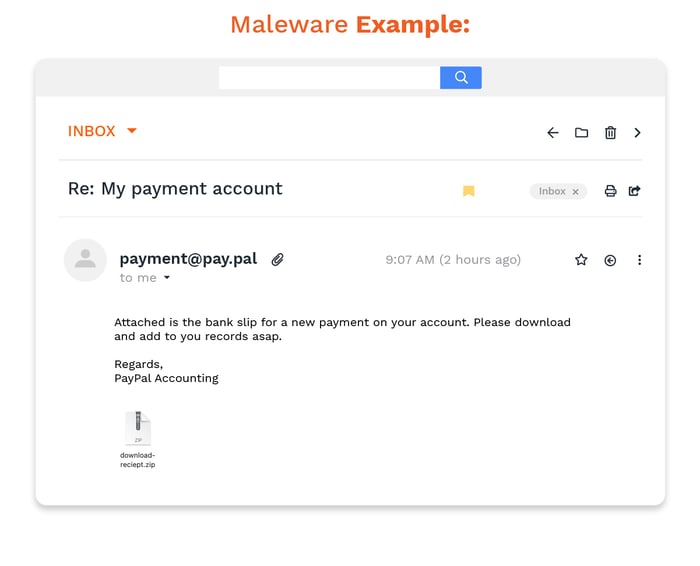
Botnet & DDoS
Botnets are groups of devices controlled by a hacker and used for widescale spam and phishing campaigns. You can also see these used in attempts to overload the systems (also known as a Distributed Denial of Service attack). The more disruption, the more likely it is for a hacker to find their way into the network and the more chaos they create.
True email security boils down to a mix of both human and technological prevention. Essentially, you’re trying to block any threats before they even make it into an inbox and still have enough wherewithal to resist the few that make it past the barriers.
How can you spot email threats?
First of all, be sure to regard ALL emails that demand payment with hesitation. If the business email appears to be from a legitimate organization such as a bank or cable company, always double-check whether or not this email is valid with the company. If the inbound email appears to be from a random address or from someone you don’t know, then you shouldn’t trust it.
As a general rule of thumb, wiring money or paying through bitcoin are the most common ways for scammers and cybercriminals to steal your money, so you should also be wary about using these payment methods for any transaction. And, of course, never open attachments from anyone you don't trust.
Also, pay attention to spelling or grammar. Oftentimes these scam emails will have substandard messaging, and it's a telltale sign that the email is bad news. Any email communications asking for passwords, Social Security numbers, upfront deposits, or similar is typically illegitimate too.

Finally, watch for any emails that claim to have incriminating evidence against you. These are very serious accusations designed to make you nervous so you act quickly to get the matter resolved. Emails that make these claims and then demand payment are spammers who don't actually have any such information. Don't panic or rush do anything rash when receiving them.
If You’re the Victim of Ransomware
We recommend that you don’t pay the ransom fee. This only fuels the fire and further encourages the creation and spread of malicious emails. Plus, there’s no guarantee that the ransom will actually do anything to help the situation. Also, do not respond to any scam emails that come from an unknown origin. The interaction alone will put you under the scammer’s scrutiny and they will relentlessly exploit your curiosity to their advantage.
What’s the best way to secure your email?
Email security comes down to throwing up as many walls between you and hackers. Just as you might have multiple barriers with your physical security (e.g., guard dog, deadbolts, security alarm), you’re doing the same with your virtual security.
We’ll break this down, depending on whether you’re trying to protect commercial or personal data.
Email Security on a Company Level
Any business that handles sensitive information, such as credit card numbers, Social Security numbers, or health records, simply can’t afford to take a chance with their email service.
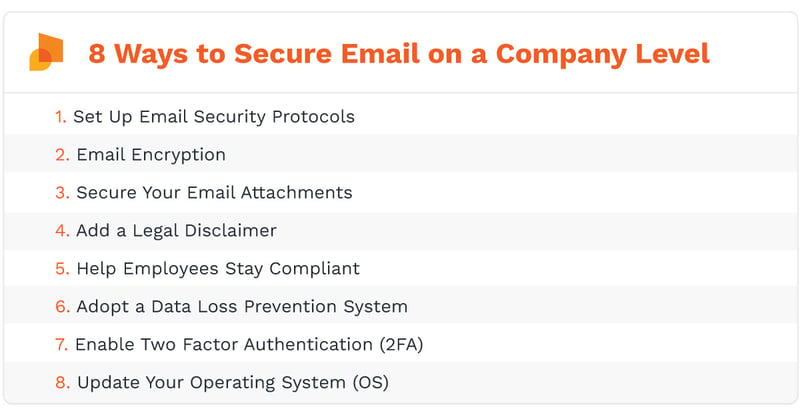
Set Up Email Security Protocols
Email security protocols essentially give an organization additional ways to keep hackers at bay, significantly lowering the odds that employees will even be confronted with the problem.
It’s critical to think ahead when it comes to email security and the right strategy can be an exceptionally effective way to do this. With these protocols, criminals can’t just use company names at their leisure, and hackers can’t just brainstorm a good subject line to entice people into solving the mystery.
It’s also an excellent way for companies to appear more legitimate to other parties. When organizations have a reliable way to verify that all outgoing messages are safe, everyone from customers to suppliers will come to see an enterprise as more reliable.
The three most used types are SPF, DKIM, and DMARC:
Sender Policy Framework (SPF)
Sender Policy Framework (SPF) searches for and blocks spoof emails. It’s an open standard validation that uncovers and verifies the origins of the sender to cull the number of potentially dangerous messages.
SPF is used by the mail exchanger to check if the domain is safe to accept messages. If the domain can’t be verified, this protocol will block the message from entering the recipient’s inbox. The goal of SPF is to remove the temptation for employees to see what lies behind the subject line.
This protocol is known as a TXT record, which essentially makes it difficult to impersonate someone else. So if a hacker is attempting a social engineering scam where they pretend to be the CEO of the company, it would be extremely difficult for their message to be pushed through to an employee’s inbox.
DomainKeys Identified Mail (DKIM)
DomainKeys Identified Mail (DKIM) is another TXT record email protocol, one that verifies a domain name using public-key cryptography. The email servers and the communications are checked using pairs of public and private keys. It ensures that each message received is either owned by the sender or verified by the owner of the domain.
The goal of DKIM is to ensure that all incoming emails are safe and that all outgoing messages make it to the recipient without interference from outside parties. Each message has an identifier (e.g., the From line, etc.) that allows the recipient to quickly determine whether the sender is an authorized party.
DKIM gives organizations some peace of mind that the incoming messages — whether from a single domain or multiple domains — are safe to open and read. This email protocol can also be configured to always allow messages from trusted senders.
Domain-based Message Authentication (DMARC)
Domain-based Message Authentication, Reporting, and Conformance (DMARC) is a blend of SPF and DKIM in a single framework. It determines whether the domain used is what the recipient sees when they receive the message. For instance, if someone sends a message claiming to be Google, the DMARC protocol would verify whether the domain is actually owned by the famous search engine before determining what to do with the message.
There are a few standard policies used with DMARC:
- None: A none policy means that all emails sent from a given domain are treated the same.
- Quarantine: This policy diverts an email from the inbox, typically sending it into a Spam folder.
- Reject: A reject policy will eliminate the message entirely, meaning it will never reach the recipient.
So with a none policy, DMARC might mark all emails coming from the CTO of a vendor as safe (regardless of what is sent). Quarantine will use predetermined conditions for what is Spam and what isn’t. This policy may mean that an important message does end up in Spam, but that it ultimately can be retrieved. A reject message will not be received by the addressee because it’s been deemed either dangerous or inconsequential.
The purpose of DMARC is to have both parties (the sender and recipient) collaborating to verify all communication. The protocol works by integrating an identity check for any received message. Because it combines the two, this protocol is typically considered the most effective for anti-phishing and anti-spoofing.
Email Encryption
Any email sent over the web is at risk of being intercepted by an attacker while en route between sender and recipient.
Encryption works by scrambling the original content of an email into an unreadable mess, with the true message only revealed with authentication from the recipient. So even if you send an email to the wrong address, the recipient won’t be able to read it.
You can encrypt through secure email hosting services or web-based encryption services. Gmail, Microsoft Outlook/Office 365, Android, and webmail all have options to encrypt emails built right into the platform. Keep in mind that the emails you send aren’t the only things that should be encrypted — the connection from your email provider, as well as stored, cached or email archiving should also be secured.
Secure Your Email Attachments
More likely than not, your outbound email attachments hold even more valuable information than the email itself. Even if the email has been encrypted, you should encrypt your attachments too.
This not only prevents them from being hacked while in transit, but prevents the recipient from saving or forwarding attachments to unauthorized employees or outsiders.
For word documents, you can encrypt the file with a password before sending it out. PDF files are a little trickier. You can set passwords for PDFs using Adobe Acrobat and OS X. However, if these aren’t an option for your company, try plugins such as Vitrium or Jira.
Add a Legal Disclaimer
Never assume a recipient is aware that the data they received is confidential.
Avoid an embarrassing (and potentially damaging) mess by including a disclaimer at the top of any email that contains private data. Health records, legal contracts, finance records, confidential industry information: these all need a disclaimer in place. In fact, disclaimers are usually a legal requirement.
While there are some limitations to disclaimers in terms of acceptance, they may hold up in a legal dispute better than you might think. The key is to ensure that your disclaimer is both relevant to and approved by the compliance officials in your industry.
Help Employees Stay Compliant
It doesn’t matter if you have the best security policies or the strongest encryption — without the right training, it’s only a matter of time until cyber threats breach your organization.
- Make sure employees understand what sensitive data is and when they’re most likely to come across it. Awareness training can go a long way to making people more alert while at work.
- Research all compliance legislation regarding your industry if you aren’t already aware. Health and legal agencies are under strict regulations, but every industry has a security standard to follow. Remember that these regulations are always changing, so have a system in place to keep up with the latest news.
- Set rules and guidelines regarding work email security. The government may have their own set of rules, but your office should have its own distinct guidelines regarding email. Ideally, you’re looking for a set of policies that address multiple concerns at once. Often, making a broad rule (e.g. “human resources are not allowed to email any personal identifying information”) and listing exceptions is easier than writing out each prohibition. Make sure all emails are work-related and never used for personal transactions.
Adopt a Data Loss Prevention System
Taking precautions to secure your emails is crucial to preventing email data loss, but all these extra steps can slow workflow. To optimize security without sacrificing your employee’s valuable time, consider investing in a data loss prevention system (DLP) that manages all sensitive data in your network — including your emails.
A DLP system identifies and monitors (in real-time)any information that is in use or in motion on your network, as well as data at rest in your storage area or on any hardware device (e.g., tablets, desktops, etc.).
Enable Two Factor Authentication (2FA)
While strong passwords are a good deterrent, hackers who target small businesses are sophisticated enough to subvert these rudimentary security measures. To kick a business’s email security up a notch, look into Two-Factor Authentication.
The 2FA protocol requires that users have a third piece of information on top of the basic username/password—usually a PIN or a code sent via mobile. These systems are common in cloud-based email servers like Gmail and are an effective way for businesses to tighten up their access points from end-to-end, email included.
Update Your Operating System (OS)
As much of a hassle as updates can be, updates exist for a reason. When your software is patched, it’s usually to correct a vulnerability or inefficiency that has already been confirmed. For example, the WannaCry Ransom Attack that affected more than 200,000 computer systems was due to a vulnerability that was later corrected.
If a person hadn’t updated their OS though, they were still at risk of being hacked. Stay on top of your IT teams and keep every operating system up to date. Email data breaches often go unnoticed for weeks or months after they occur and can be devastating to a company’s public image and profitability from quarter to quarter.
Email Security at a User Level
Individual users should be aware of email security and take the following steps to keep both their information and network safe.
Never Download Attachments from an Unreputable Source
Never view or download attachments from a sender you don't know. Even if you do know them, check with the sender to verify the message if you weren’t expecting an attachment. Oftentimes, criminals will abuse your online address book and send you an email pretending to be someone you have exchanged emails with in the past.
Turn ON Your Spam Filter
People might turn off their spam filtering to avoid missing important email messages, as they are known to be sent to the wrong box. However, instead of turning the filter back on, they forget and leave it off. The filter may not seem like much of a protector, but it’s actually a great first line of defense against potential threats.
Watch Your Passwords
In addition to changing your passwords regularly, you should also have different passwords for every account to limit your overall risk. Third-party software like Last Pass can work for personal use, but we still recommend the old-fashioned technique of writing down your passwords and storing them offline. Keeping them stored on your computer is like leaving the back door to your house open and hoping no one breaks in
Use a Reputable Antivirus Program
Have an up-to-date anti-virus program running at all times. Browsing the Internet without an antivirus program that includes web and email protection leaves you vulnerable to ransomware programs, which are the perfect tools for blackmailing businesses and individuals alike. Lack of protection from these antivirus programs allows criminals to access your information and violate your privacy.
Should You Outsource Your Email Security Solutions?
This one is not a cut-and-dry answer. Here’s what to keep in mind before you sign up for a specialty service.
The Advantages of Outsourcing
People typically outsource email security because they don’t want to invest either the time or money. Obtaining the necessary infrastructure, keeping it up to date and devising a management structure takes a lot of work, particularly for larger companies. The above suggestions require plenty of fine-tuning and readjustment, and not everyone can afford to spend that much when implementing their security strategy.
So not only could you reduce the capital you’re spending when you outsource, but you also reduce the demands on your systems, network, and staff. The good news is that outsourcing security risks can mean more flexibility. These services are designed to handle spikes in email traffic as well as archiving and outbound messages.
The Disadvantages of Outsourcing
The most obvious disadvantage of outsourcing your email security services is that you don’t always know what’s happening with your security: you are giving up control. In many cases, this is the smartest decision you can make, but you will need to be aware of mistakes that may take place without your knowledge. Maybe those mistakes are corrected before they affect you — but sometimes they aren’t.
Also, be aware that outsourcing can have more than one bottom line. The best advice is to really research any vendor you might do business with to ensure they have the technical expertise and business management skills needed.
How can you find the best email security solution for you?
Avoiding email attacks will mean looking at your situation objectively and assessing what company or personal breach would mean for you. Network security and threat intelligence have to account for everything from human error to outdated hardware.
It becomes a question of whether you have the personal bandwidth or resources to get it all done. On-premises security services will mean giving up some degree of control, but outsourced cloud security for your emails can potentially improve your protection while reducing your investment.
Whichever decision you make, just remember that your efforts are more than worth the rewards. If you can properly integrate all of our suggestions, you will drastically cut down your odds of harmful data leaks. The data protection will apply to both incoming and outgoing emails, which can be a huge relief for anyone.
Categories: Security, Malware, Cyber Crime, Online Scams, Email, IT Management, Proactive Network Security, Cloud Computing Security, IT Security, Phishing, Email Security











