
We were inspired to create this because we see too many security misconceptions from our current and future customers. Misconceptions like:
In the end, you're holding in your hands (or, more likely, reading on your screen) the information you need to overcome those misconceptions about information security with the truth. This eBook contains a compilation of security trends that affect businesses of every size, but that can hit small and medium businesses harder than larger companies.
Whether you're an IT security pro, business owner, or are responsible for IT in your company; the six security trends in this ebook will impact you. While every business should be concerned about security, securing your network and information shouldn't be a scary process.
Before we dive in, we want to be crystal clear on the following four points:
1: Security threats ARE scary.
Both personally and professionally, cybercriminals are attempting to hack into and steal your information. That's a simple fact of life today. How you choose to respond to those threats will be the difference between being aware and concerned versus not knowing and being scared (or remaining ignorant, which is REALLY scary). You need to understand that SMBs are NOT too small for cybercriminals to target.
2: If some of the following comes over as fear-mongering, that's not our goal.
We aren't trying to be scary for the sake of being scary. As a company, we also worry about and spend time confronting these same security threats and challenges.
3: When you understand security threats and trends, securing your networks and information IS possible!
You can implement the right tools to deflect and deter those threats – on your own or with a managed network services partner.
4: Security is never-ending.
A proactive approach will help you sleep well at night knowing your business is protected. However, ongoing vigilance is required. You are never “finished” with security. You will need to continually adapt your security strategy to meet new threats.
If you have the internal resources – technical and financial – you can handle network security yourself. You don't need us or any of the other managed IT providers out there.
 If you don't have the resources (or realize and act on these threats); your business can be extremely vulnerable to hackers and assorted cybercriminals.
If you don't have the resources (or realize and act on these threats); your business can be extremely vulnerable to hackers and assorted cybercriminals.
In this short ebook, we will help you understand six security trends and issues that affect SMBs. Then we will share thoughts on how you can lock up your information and network by outsourcing.
Even if you don't think outsourcing is right for you, keep reading to learn about the security challenges your company is facing because whether you know about them or not, cybercriminals are stalking you (and us, and every business out there). We'll also share a few security tips you can begin implementing immediately as well as introduce the idea of managed IT.
If you stop reading now, remember this: no business is small enough to avoid a cyber attack and you don't have to be a security expert yourself (or have one on staff) to protect yourself.
Before we get to the trends though, we want you to answer a question.


Ask yourself this critical question:
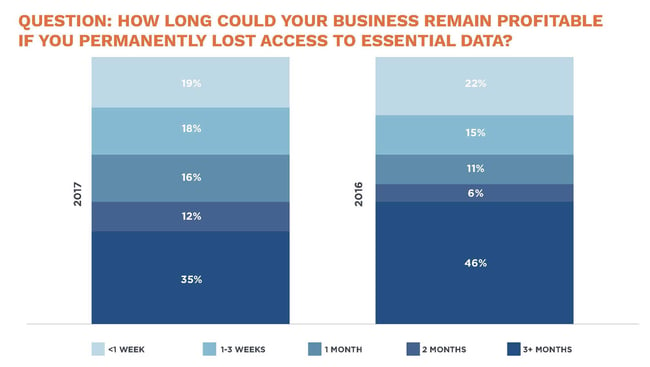
How long could your business remain profitable
if you permanently lost access to essential data?
If you're like most SMBs, you wouldn't remain profitable for long. This question gets to the heart of why every business needs information security. Your business relies on continued access to its business documents and other information.
The true benefit of planning for security is the ability to remain profitable after a cyber breach that results in major data loss.
Depending on your business, you could lose hundreds to tens of thousands of dollars in revenue for every hour your network is down.
If a cyber attack locked you out of your data – that's what ransomware does – and you didn't have a reliable data backup strategy, all of your digital company data could be gone.
 That statement might seem extreme. It's not. Ransomware is designed to prevent a business from accessing its data. Attempt to delete the ransomware, and the ransomware deletes your data.
That statement might seem extreme. It's not. Ransomware is designed to prevent a business from accessing its data. Attempt to delete the ransomware, and the ransomware deletes your data.
In addition to your lost data, your brand could be damaged, customers could lose trust in your business, and it costs both time and money to repair your network and restart from your back up data.
Without tight information security plans and policies in place, you are at risk of going out of business.
No one invests in information security for fun – though cybersecurity pros do enjoy the challenge of keeping businesses secure.
You lock the doors to your office building. You need to do the same to your network and information.
Source: The 2017 State of SMB Cybersecurity
As you read the rest of this ebook, keep this question in the back of your mind. Security is that important to your business.
The dramatic increase in security issues boils down to one thing: money.
Cybercriminals make money from businesses and individuals who don't keep their data secure.

Overall, cybercrime will cost the world $6 trillion by 2021 – that's more profitable than the global trade of illegal drugs.
Ransomware is a $5 billion industry. Hackers are thieves. They go where the easy money is. SMBs are easy money. There are ransomware kits for sale online on the Dark Web (there really is a Dark Web, it's not fiction).
A business falls victim to a ransomware attack every 40 seconds. By 2019, ransomware attacks on business will happen every 14 seconds. Damage from those ransomware attacks is predicted to reach $11.5 billion by 2019.
How do these enormous figures affect you?
Criminals like an unlocked door or window. Many SMBs simply can't keep up with the constant barrage of security updates, changing threats, best practices, and network and security technology and are leaving their office doors unlocked.
SMBs that attempt to keep up with security on their own can find themselves overwhelmed. Worse, IT initiatives that are key to creating business efficiency and competitive advantage – using a copier's scanning functionality to automate a business process like accounts payable, for example – never get implemented.
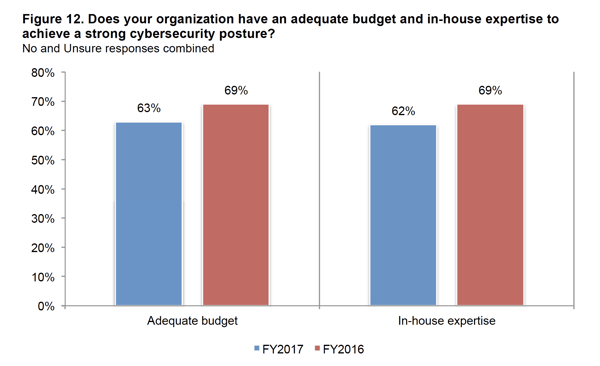
The Ponemon Institute provides yearly research on SMB security. Their most recent report, 2017 State of Cybersecurity in SMBs, reveals an increase in attacks, and the costs of successful breaches:

Overall, 62% of ALL cyber attacks target SMBs.
We aren't sharing these numbers to scare you. We are trying to show you that cyber security is a problem for EVERY business – no matter how large or small.

These six trends and issues hit SMBs particularly hard because most SMBs lack the internal resources to keep up with the security challenges these trends cause.
These two issues are intertwined.
Security and malware are engaged in a constant back and forth of punch and counterpunch. Whenever a hacker finds a hole to exploit with a virus, the antivirus companies write software to close that hole. That's why you need to update your antivirus software constantly.
Software and hardware companies releases patches weekly. These patches update security holes and improve operation. When you miss applying an update, you leave a window open for a hacker.
 On a personal level, keeping devices up-to-date with antivirus software is a chore. For a business, every laptop needs to be updated, the firewall patched and updated, any mobile devices used to access business information need to be secured – and that's only a short list.
On a personal level, keeping devices up-to-date with antivirus software is a chore. For a business, every laptop needs to be updated, the firewall patched and updated, any mobile devices used to access business information need to be secured – and that's only a short list.
Malware evolves quickly. Ransomware families tripled to 101 in 2016. In 2014, there were 275 million variations of malware. In 2016, there were 327 million. Symantec noted an increase in antivirus detections in 2016, from 846/day to 1,539 each day by the end of the year. The number is higher, as most attacks were blocked earlier in the infection process (and this is limited to Symantec antivirus technology).
How important is it to keep patches up-to-date? The WannaCry virus from 2017 exploited a known security hole in Windows that Microsoft had issued a patch for months before the virus brought IT systems in hospitals in the UK and businesses across Europe and the United States to their knees
There aren't enough cybersecurity experts for all of the open cybersecurity jobs.
In 2004, there were 1 million unfilled security jobs worldwide. There were about 350,000 cybersecurity job openings in the U.S. In 2017. By 2021, there will be at least 500,000 unfilled cybersecurity positions. That's only the United States. There will be another 3 million unfilled cybersecurity positions globally. The cybersecurity unemployment rate will effectively be 0%.
As with any scarce resource, acquiring cybersecurity experts costs more. The median cybersecurity salary is 2.7 times the average wage. In the US, IT security pros earn a 9% salary premium.
As the gap widens, it's going to difficult for SMBs to pay enough to keep good cybersecurity professionals on staff.

There's no way an SMB's IT staff can monitor the network 24/7. They can set up firewalls and antivirus software as well as alerts, but at some point they will call in sick or want to go on vacation – or simply need to sleep!
Malware attacks occur around the clock. Proactive network monitoring means that a network is constantly monitored to detect and deter attacks. Instead of an alert that might not be addressed for hours (during which time your network could be compromised), proactive network monitoring identifies and then can block a security exploit before it can get into your system and cause any damage.
The best part about network monitoring when you outsource it is that you never know if your network was attacked until your read the report from your managed IT partner. Your service provider will detect and remediate security issues, including updating patches to protect you from further vulnerability.
All this means less downtime for your office plus more relaxed sleep for your IT staff – and more productivity from them as well as they work to proactively improve your IT operations rather than react to hacker attacks every day.

Backing up data is the single best defense against ransomware or a network outage.
 Backing up data is also tedious, many businesses don't do it, and many business that do backup data don't check to make sure they did it right.
Backing up data is also tedious, many businesses don't do it, and many business that do backup data don't check to make sure they did it right.
The number one SMB data backup mistake is not having a backup plan.
Even without the threats posed by cybercriminals, at some point every hard drive or server will fail. That's just a simple fact. For companies with limited IT staff, backup is often forgotten:
If you're locked out of your data by ransomware, you can restore your systems from backup. You'll lose some time and data (depending on how frequently you backup your data), but you won't be held for ransom and you'll be able to get back to work quickly.

By the time most in-house IT teams reach the end of another day of patching and trouble-shooting, they haven't been able to devote the time to thinking strategically about IT.
It's a cliché, but technology is constantly changing. Wasting time managing a ne
twork that could be outsourced means less time planning how to take advantage of new IT tools and strategies to advance your business.
Think about it. You could change the oil in your car if you – buy the oil and the filter, have a flat area you can drain the oil on, have all of the needed tools, and then you'd have to dispose of the oil.
Or you could drive to Jiffy Lube and be finished in 30 minutes and spend the time in the waiting room reading a book or working on a business plan.
Your IT staff could manage your network, but the time it takes them to do so means they have less time to devote to higher-value planning and optimization. When your IT team is focused on ensuring the day-to-day IT infrastructure is working, they aren't able to take the time to sit back and think through what additional IT infrastructure is needed and how to optimize it for the business. What new technology do you need? New computers, servers, email system, collaboration tool, firewalls, etc. – and which one is the most important? What can wait for six months? What don't you need at all?
Outsourcing network management and backup allows an internal IT team to establish their roadmap for the future. A managed IT partner can also help you with goal-setting if you lack the strategic vision internally. Just because your in-house IT person is a whiz at troubleshooting PCs and managing your network doesn't mean they have the knowledge, skill, or expertise to understand IT trends and how to map them to your business needs.
Regardless, every business needs to plan their IT needs for today and plan for future IT infrastructure needs.


We hope we've changed your mind about the importance of planning for security in your business – you aren't too small to be hacked!
You also have plenty to think about as you decide how to best secure your business' information assets and network.
You can invest in the staff and tools and do this yourself.
Just remember that you don't have to.
These six trends are affecting businesses everywhere.
How did you do at answering our questions:
 We're going to guess you answered “no” to at least one of those – maybe more. That's OK. You have to understand where you are so you can improve.
We're going to guess you answered “no” to at least one of those – maybe more. That's OK. You have to understand where you are so you can improve.
Meeting your business' security needs doesn't have to be intimidating. There are three steps you can take that will begin your cybersecurity journey:
Smaller in-house IT teams are often overwhelmed. To grow, all businesses need a stable IT infrastructure. The ability to scale IT infrastructure to support the growth you want can overwhelm even experienced IT pros – managing patches, maintaining servers, keeping the company website online, troubleshooting user accounts, network monitoring, backup management, and service desk support for users are just a few of the tasks that confront IT teams daily.
When your internal IT team is struggling to keep up:

Over time, these challenges can compound so that an in-house IT team is running full speed just to slightly behind where they need to be for network security upgrades and planning.
The first line of defense against cyber attacks is a well-managed and secured network. Outsourcing your network management and data backup to a managed IT partner provides many benefits:
Now that you know and understand the security challenges and trends facing your business, you can overcome them.
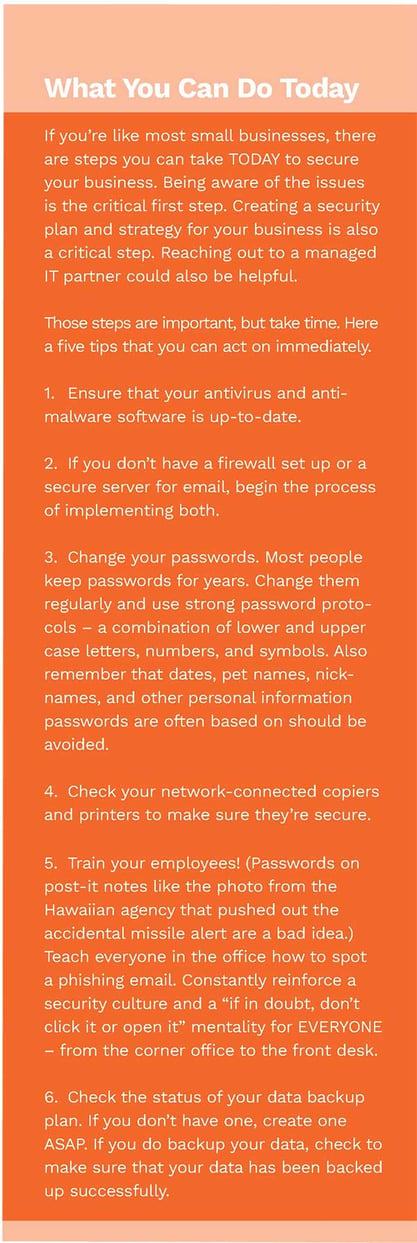
Get started immediately with the tips we provided above. Then begin the more difficult task of putting a security plan in place.
Sources:.
Related Information